Why Lacework is a Leader in the KuppingerCole Leadership Compass for CNAPP
Lacework
FEBRUARY 1, 2024
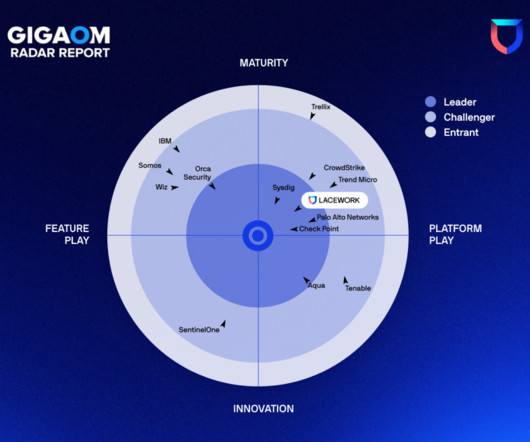
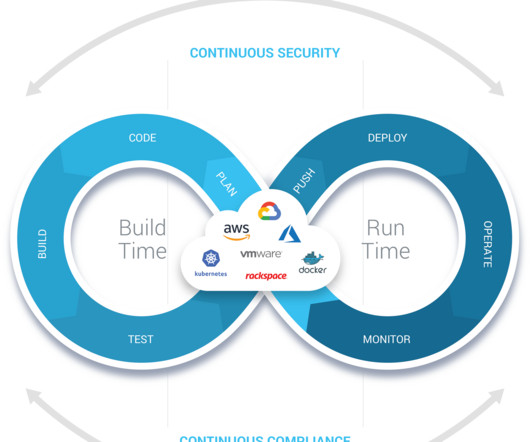
At Lacework, we believe that true CNAPPs are built on a unified platform and effectively combine risk mitigation and threat management — and that’s exactly why we’re being recognized as a leading CNAPP solution. CNAPPs like Lacework were created to solve and simplify this problem. Why Lacework?














































Let's personalize your content