New integration with Kubernetes admissions controller
Nolan Karpinski and Joe Goldberg

Lacework for Kubernetes 101
Kubernetes is a popular open source platform that automates the deployment and
management of containerized applications. As development teams increase their
Kubernetes usage, they’re shipping and scaling their workloads faster than
ever before. However, Kubernetes also needs to be properly monitored and
secured to prevent an external threat or malicious insider from compromising
containers and the workloads within them. This compromise could lead to
nefarious activities such as cryptomining, or finding and exfiltrating
sensitive data.
Lacework was built for cloud security with the ability to handle the complex and temporary nature of containers and cloud resources at unlimited scale. This includes comprehensive visibility, threat detection and alerts, and compliance checks on your entire Kubernetes environment including clusters, nodes, pods, containers and the control plane. This protection spans all the stages of Kubernetes cloud infrastructure deployment, from build-time to runtime. We also provide automated, embedded capabilities, such as container scanning, into developer workflows. This enables security to “shift-left” into the develop and build stages while not getting in the way of development efforts. Lastly, Lacework offers automated anomaly and threat detection in runtime with our patented Polygraph unsupervised machine learning, so little to no time is spent writing threat detection rules and false positives are rare.
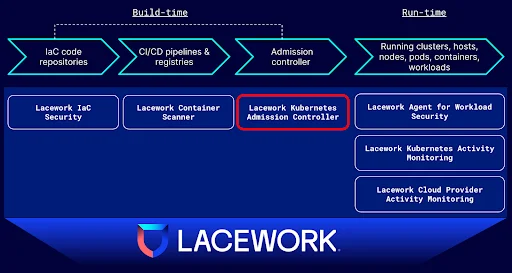
Figure 1: Lacework protects across all stages of Kubernetes usage, including the Kubernetes Admission Controller
The Kubernetes admission controller
Kubernetes admission controllers are plugins that govern and enforce how a
cluster is used and what is allowed to run on a cluster. They act as
gatekeepers that intercept authenticated Kubernetes API requests. While there
are several admission controllers shipped with Kubernetes, one that is very
important for security purposes is the validating admission webhook which can
either allow or reject a request (validation). This admissions controller does
not implement policy decision logic. Instead, the Kubernetes API obtains
actions from a REST endpoint (a webhook) of a service running in the cluster.
This approach decouples admission control logic from the Kubernetes API
server, allowing users to implement custom logic to execute whenever resources
are created, updated, or deleted in a Kubernetes cluster.
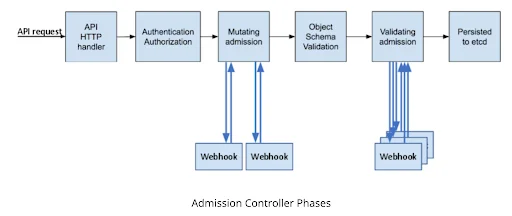
Figure 2: Admission Controller phases, including the validating admission phase
New! Integration with the Kubernetes admission controller
Lacework now has the ability to integrate with the Kubernetes Admission
Controller so prior to containers being deployed onto Kubernetes in
production, Lacework scans them for misconfigurations or vulnerabilities. If
insecure containers are found, based on policies Lacework can optionally
instruct the Admissions Controller to block these containers from being
deployed. This greatly reduces the risk of a misconfiguration or vulnerability
existing in production that a threat could exploit or use as an ingress point,
which means that you’ll spend less time and money fixing downstream issues in
production.
While other cloud security platforms can integrate with Kubernetes admission controllers, Lacework is unique because it has a single set of policies that apply consistently across all images and all Lacework container scanning modes (e.g., inline, proxy, platform), delivered via a single, comprehensive cloud security platform. And our integration is proven at scale as we have customers using it to run more than 100,000 weekly container scans.
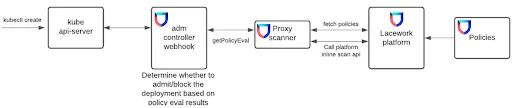
Figure 3: Lacework integration with the Kubernetes admission control. The Lacework shield logo represents Lacework technology and logic
Per the diagram above, and as detailed in our Documentation, Lacework uses our validating admission webhook to integrate with the Kubernetes admission controller to then automatically scan images for vulnerabilities and enforce security policies during continuous deployment. We do the scan via our proxy scanner. Lacework recommends using a combined Helm Chart—a collection of files describing a related set of Kubernetes resources—to install the Lacework proxy scanner and webhook together in a Kubernetes cluster on the same host to allow communication between Lacework and the Kubernetes admission controller. After installing the proxy scanner and webhook, you need to associate policies with a registry integration or vice versa in Lacework to determine where to pull images from.
The Lacework proxy scanner fetches and applies container vulnerability policies from the Lacework platform and these policies are applied to assess the container images and what actions to take when specific criteria are met. Lacework ships with pre-built container policies or customers can create their own custom policies.
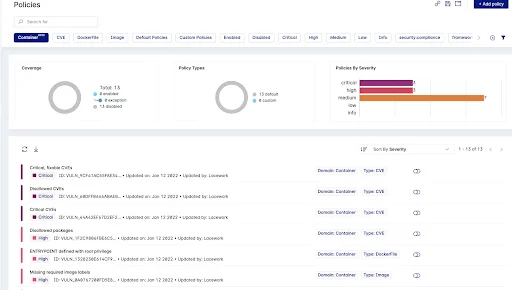
Figure 4: Several container policies as shown in the Lacework UI
After a container scan, the policy evaluation results from Lacework are sent back to the Kubernetes admission controller which uses the Action on failure field to allow or block a container in violation of the policy.
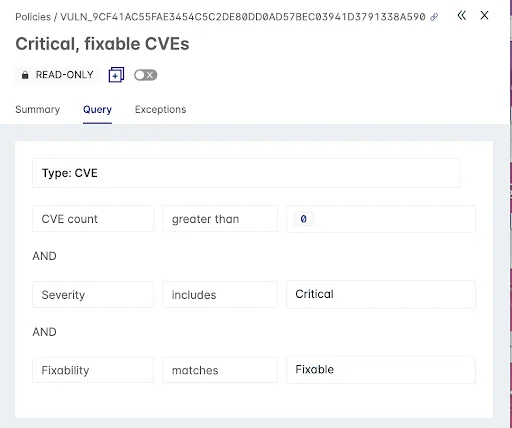
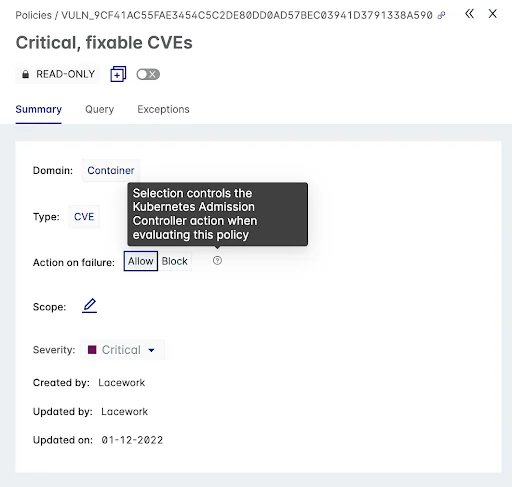
Figure 5: Within each container policy, the violation criteria and associated actions on failure of Allow or Block are defined
You might be wondering if you are already performing container scans within your CI/CD pipeline, why do you need to still scan them via Lacework integration with the Kubernetes admission controller. The answer goes back to defense in depth as the Kubernetes integration is essential as a secondary check to catch risks like:
- Public, manually deployed, or rogue containers that bypass CI/CD pipelines.
- Infrastructure-related images such as Google Kubernetes Engine (GKE) worker pods that also bypass CI/CD pipelines
- Development teams that deploy images from non-trusted container registries
This layered defense is also efficient from a scanning perspective. Lacework can initially look at the container hash to determine if it has already been scanned and approved by a different Lacework scanner such as the inline scanner within a CI/CD pipeline. If so, Lacework can tell the Kubernetes admission controller to let it through to production without needing to rescan it.
In summary, Lacework integration with the Kubernetes admission controller helps ensure only secure containers are deployed on Kubernetes. You can rest easier knowing your container security and compliance posture is enhanced with automated and continuous protection.
Learn more about Kubernetes security.
In addition to
Lacework’s new Kubernetes Audit Logs Monitoring feature, demonstrates our ongoing commitment to enhancing Kubernetes security for
our customers to provide end-to-end integrated monitoring and protection of
your Kubernetes environment.
Learn more about how Lacework helps with Kubernetes security by reading our Kubernetes web page and solutions brief, or contact Sales to see a live demo.
Categories
Suggested for you