New custom risk score cuts vulnerability noise by up to 90 percent
Editor’s note: This blog announces the release of the newest platform enhancement from Lacework, which introduces custom risk-based vulnerability scoring. The Polygraph® Data Platform uniquely combines active vulnerability detection, attack path analysis, active exploit data, and novel research by Lacework Labs so you can safely reduce 90% of vulnerability noise and ensure your teams focus on what matters most.
Automation can drive down costs, improve response times, and deliver massive gains in operational efficiency. And automation has impacted every industry, as we enter what many are calling the “fourth industrial revolution” — a movement defined by big data analytics, machine learning, cloud computing, predictive maintenance, robotics, and the like.
In the fourth industrial revolution, the ability to use automation effectively is the key to increasing productivity, accelerating business growth, and maximizing cost savings. Yet while we’re expected to take advantage of every new innovation and speed ahead, we’re often blind of the risks. Consider the cloud. Organizations have been quick to adopt the gains of the cloud but have been slower to automate security in a way that is accurate, effective, and improves productivity.
For security teams, automation is critical. The stakes are high, the risks are real, the bandwidth is low, and the consequences are painful. There has never been a greater need to establish a more automated and dependable approach to cloud security.
New Lacework automation simplifies risk management for your entire company
Organizations need actionable risk data that is reliable, rooted in their own information, and customized for their own environment. Otherwise, teams will — and do — find themselves solving for “critical” cloud risks that, in reality, will have no material impact on their environment. This situation harms the security teams responsible for investigating the issues, the developers tasked with fixing the issues, and the trust that exists between those two teams.
Lacework is now using automation to help organizations gain control of their vulnerability risk management program and increase operational efficiencies. Customers can now gain risk-based vulnerability scores that are specific to their environment, without requiring them to manage complex data sets or write and maintain custom logic. This new platform enhancement will eliminate repetitive, mundane tasks and reduce the burden on overworked teams.
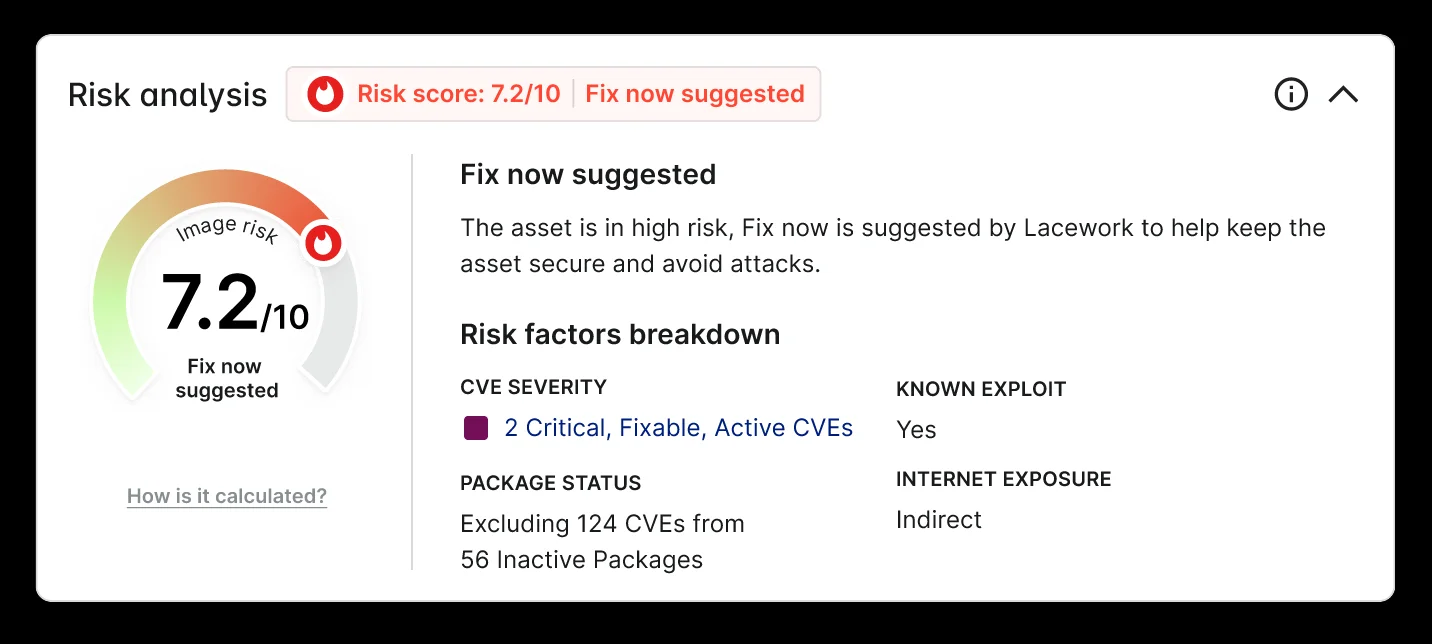
Figure 1: Risk-based vulnerability score
Too many vulnerabilities, the welcome mat for breaches
Risk management programs need an upgrade. Security teams are inundated with endless queues of alerts from cloud risks. Third-party feeds help rank the danger of these vulnerabilities from low to critical, but this only goes so far. The U.S. government’s National Vulnerability Database (NVD) lists a grand total of 200,000+ vulnerabilities, 18,000+ of which are listed as critical severity and 50,000 of which are listed as high severity. But, in reality, severity can vary based on the unique cloud environment. Severity depends on vulnerability impact, likelihood of exploitation, and at-risk asset criticality, among other factors.
Strained and short staffed teams don’t have enough time to manage complex data sets or create manual rules with custom logic to account for every possible risky scenario. It’s simply not scalable for an infinite attack surface like the cloud. It’s too resource heavy, costly, and time-consuming to analyze and fix every single vulnerability. This manual approach leaves room for error. And error leads to data breaches.
With the rise in cybercrime and cloud-based attacks, it’s understandable why security teams don’t want to get blamed for missing an alert or dismissing a false positive. This is why context becomes key. Without the right context, organizations struggle to prioritize an ever-growing volume of vulnerabilities.
How Lacework curates a custom risk-based vulnerability score
Effective vulnerability management requires a risk-based approach that goes well beyond CVSS scores or the severity provided by the NVD. Because, in reality, a “critical” vulnerability for one company may look totally different at another company.
This is where Lacework has an innovative advantage over other vendors. Our platform is already ingesting as much of your cloud data as possible and has a deep knowledge of your cloud environment. And this deep understanding, combined with novel research from Lacework Labs and third-party exploit intelligence, is now enabling us to automatically provide you with custom risk-based vulnerability scores, surfacing only your unique environment’s biggest issues.
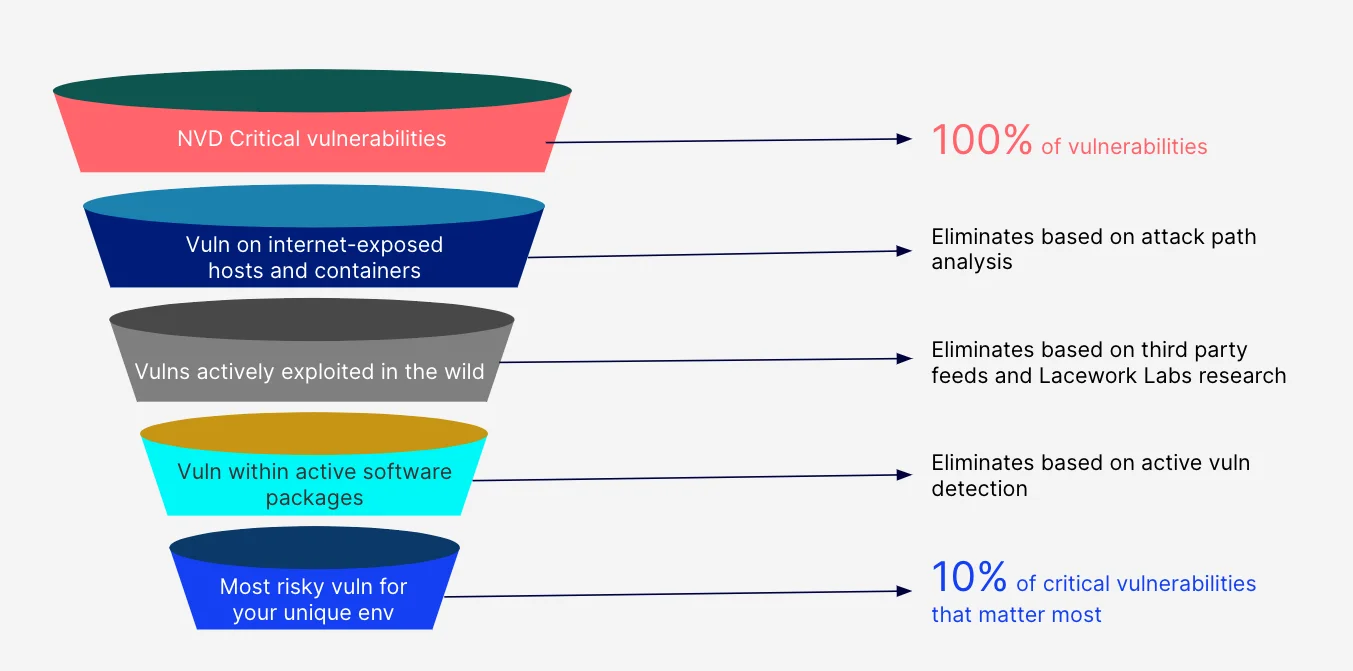
Figure 2: How the custom risk-based vulnerability score is determined
The process starts with the NVD to get a handle on critical vulnerabilities. We leverage their security checklist references, security-related software flaws, misconfigurations, product names, and, of course, impact metrics. We then incorporate CVE and CVSS data to identify vulnerabilities and their relative severity, just like every other security vendor.
But then Lacework goes to work. Our platform automatically takes your critical vulnerabilities and sifts them through a series of additional filters to help you reduce the noise and focus efforts on exploitable risks.
Unlike other security vendors, we layer on unique customer attributes, including which vulnerable software packages are active, which ones may be exposed to the internet, what critical data assets are in the vulnerability’s path, and whether active exploits exist in the wild. We combine commercially available exploit data, active vulnerability detection, and attack path analysis with innovative research from Lacework Labs to reduce critical vulnerabilities from an overwhelming number to a small group of your absolutely, positively most critical vulnerabilities.
These risk scores also adjust automatically, based on new cloud activity. We continuously monitor the file system of every cloud host. When a package is executed, the agent detects this activity. This information is both reflected in our new risk score and in the Lacework console.
And we do all of this in the background, completely unbeknownst to you. All you see is the outcome: the ability to reduce 90% of vulnerability noise. Automation at its finest.
Active vulnerability detection keeps you from barking up the wrong tree
One of the new, underlying functionalities behind the new custom risk score is active vulnerability detection. Developers are often tasked by the security team to update software that, in reality, isn’t actually running and doesn’t pose a security risk. This problem is compounded by software bloat, where developers package more software than is needed for an application to operate.
Without the right tools, when a security team notices an application vulnerability, it’s difficult to determine whether that issue in the package is actually tied to running software. Flagging inactive vulnerabilities to developers can ultimately waste time for development teams, which can naturally lead to friction with security teams.
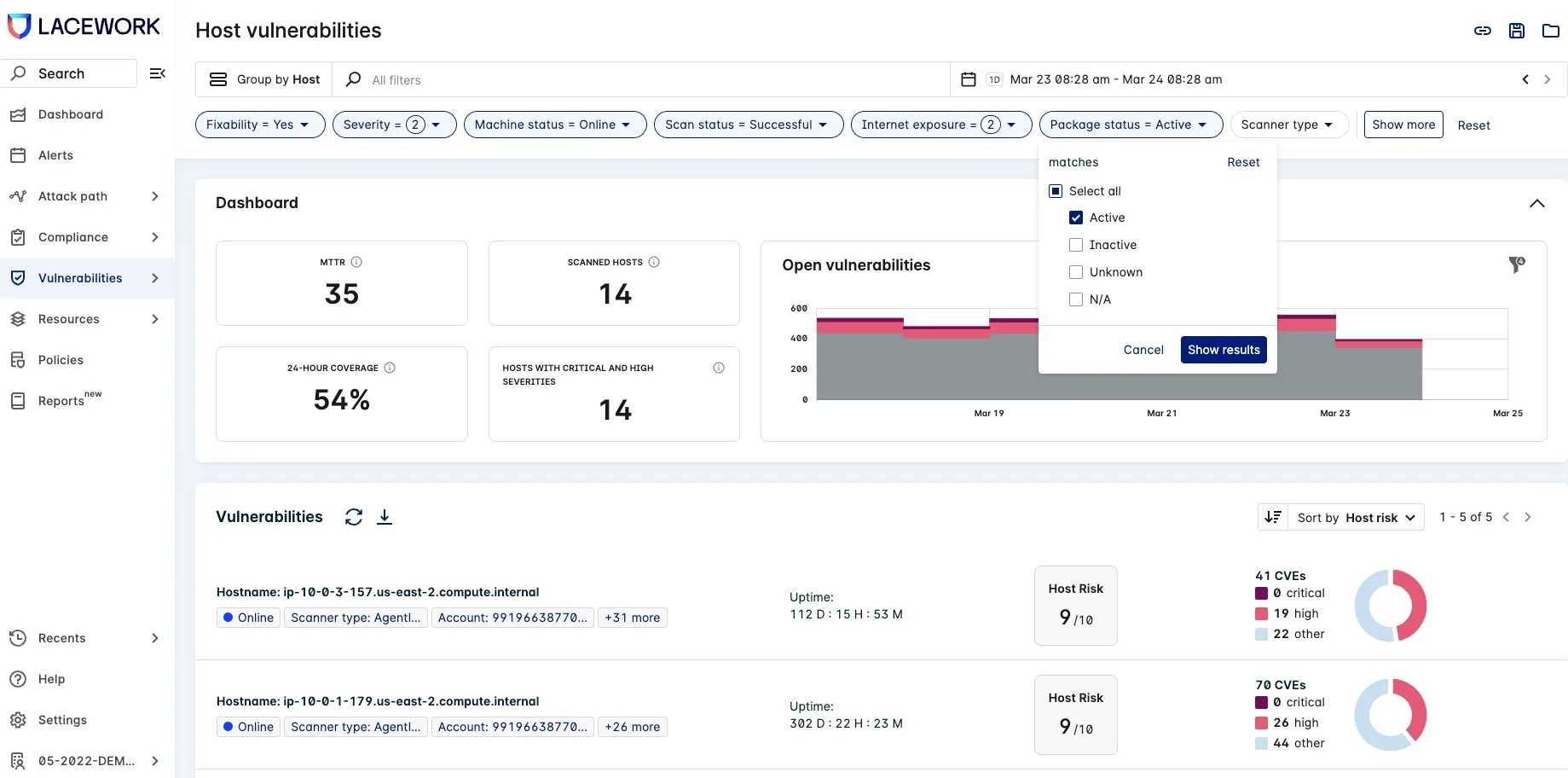
Using active vulnerability management from our agent, you can automatically identify vulnerable software packages that are active. This capability significantly reduces noise from inactive vulnerable packages and refocuses developer time on work that creates value for the business.
Figure 3: Active vulnerability detection in the vulnerabilities dashboard
Customers have been able to drastically reduce the number of NVD critical vulnerabilities to remediate. This capability gives teams the context to determine the most important items to fix that will reduce their overall risk, instead of spending time fixing vulnerabilities that don’t really matter.
See all of your attack paths in one unified place
Another underlying functionality behind our new custom risk score is our attack path analysis capability. Last year, we introduced attack path analysis into our platform. With last year’s enhancement, every alert that involved an internet-exposed vulnerability included an Exposure Polygraph visualization, displaying how bad actors could breach an environment, then move laterally to exploit data in that environment.
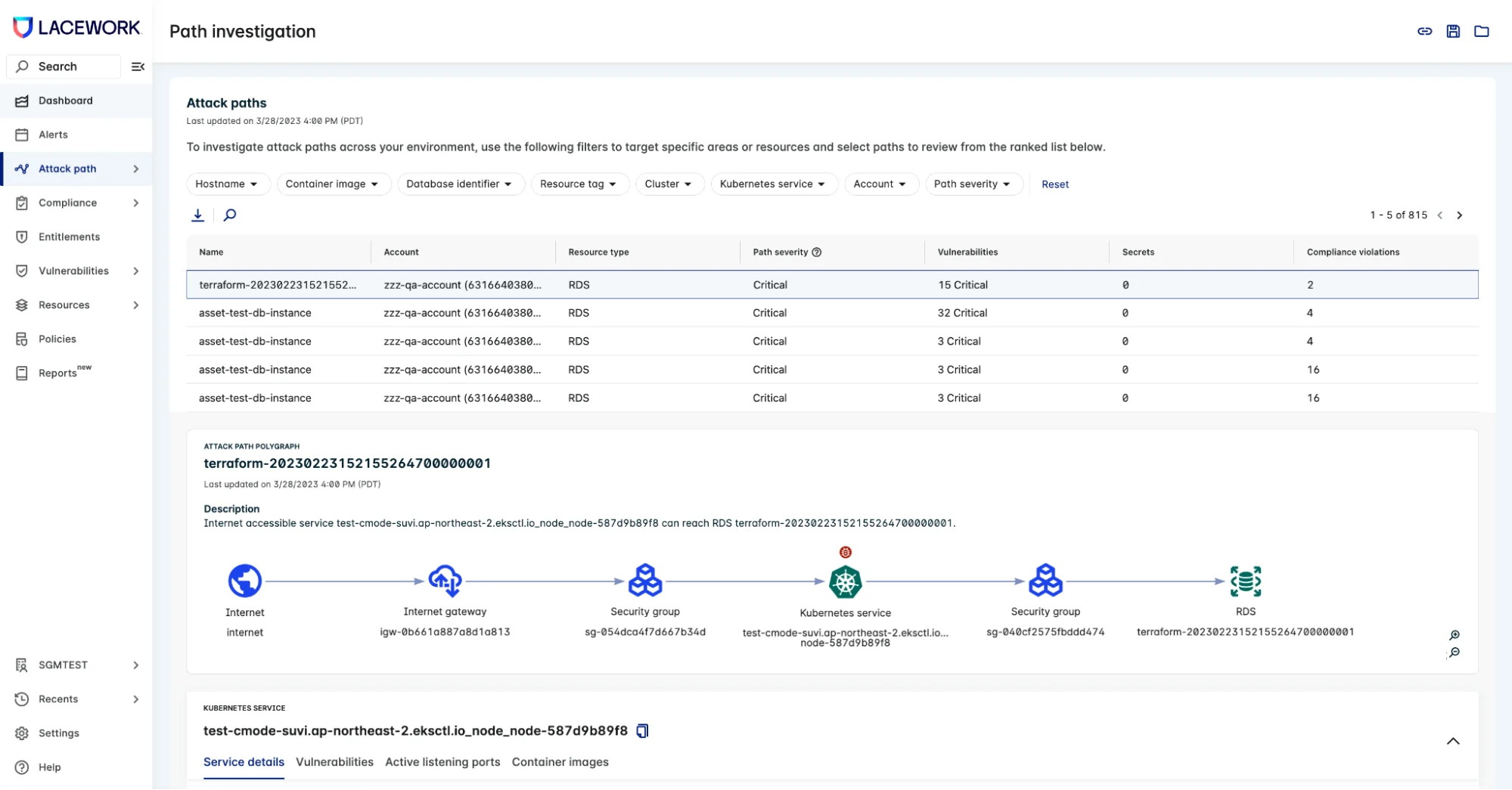
With this new release, our attack path analysis capabilities go even further. Our platform now has a dedicated dashboard, granting immediate visibility into your top risks and attack paths that lead to your most critical assets. This unified dashboard provides posture teams with an overview of the riskiest entities in their environments, helping prioritize the most impactful work items. It also helps visualize all of the ways attackers can reach critical data assets, so teams can gain an in-depth knowledge of their cloud environments.
Figure 4: Dedicated path investigation dashboard
Every attack path starts from the internet and ends with an asset like a workload, a database, or another data storage device. Last year’s platform enhancement visualized the path from the internet to the first reachable EC2 host or container image. With this release, users can now more accurately gauge the importance of fixing an attack path risk by tracing a bad actor’s steps from the internet to Amazon RDS, Amazon Aurora, and other cloud assets.
Fewer fire drills. More trust between security and development.
Now, with these new Lacework releases, organizations can:
- Reduce 90% of critical vulnerability noise. Lacework uniquely combines active vulnerability detection, attack path analysis, and commercially curated exploit feeds to reduce 9-of-10 critical vulnerabilities.
- Tailor vulnerability scores to your cloud environment. Lacework provides a risk score that reflects a customer’s specific environment, while also allowing customers to tune the score parameters to align with their unique risk tolerance requirement.
- Understand active vs. inactive vulnerabilities. Reflected in the custom risk score, the Lacework agent identifies which vulnerable software packages are active, and thus require immediate attention.
- Enable developers to spend more time coding and less time fixing security issues. By focusing on only active vulnerabilities, developers save significant time investigating and fixing vulnerabilities, freeing them to spend more time creating value for the business.
- Build a bridge between security and development: Security earns trust with DevOps by providing developers with highly accurate and actionable vulnerability data so they don’t waste time on vulnerabilities that do not actually need their attention.
For too long, innovation speed has been sacrificed for security. But now, because of smart automation, security teams can breathe easier with lighter alert queues, and development teams can rest assured that they are only working on the security issues that truly matter. A true win-win for the thousands of global companies that trust Lacework to secure their cloud environment every single day.
Interested in using Lacework to better manage vulnerabilities? Visit this page and check out our webinar to learn more.
Suggested for you