Google: Monitor These Emerging Cloud Security Challenges in 2023
Tenable
JANUARY 12, 2023
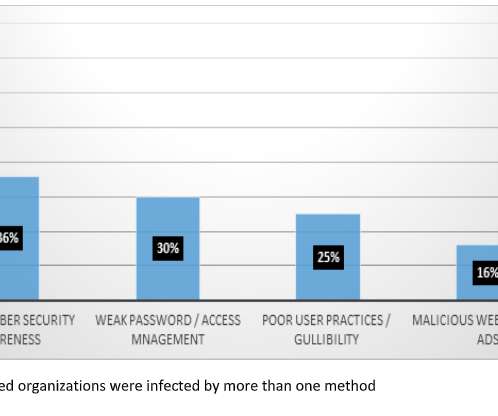
In its latest “Threat Horizons” report, Google’s Cybersecurity Action Team details cloud security trends that it expects will have an impact in 2023 in areas including identity and access management (IAM), data backups and operational technology (OT.). Cloud providers’ IP addresses and open ports targeted with malware.




















































Let's personalize your content