Cybersecurity Snapshot: New Guide Details How To Use AI Securely, as CERT Honcho Tells CISOs To Sharpen AI Security Skills Pronto
Tenable
JANUARY 26, 2024
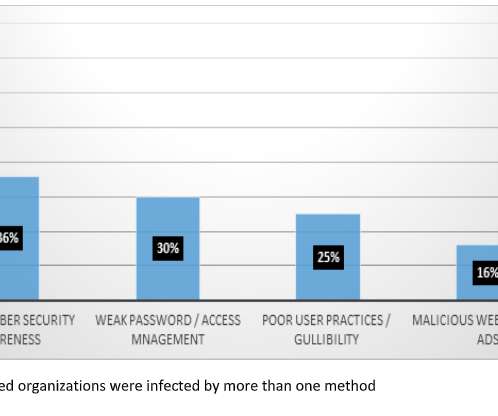
1 - Using AI securely: Global cyber agencies publish new guide Is your organization – like many others – aggressively adopting artificial intelligence to boost operational efficiency? If so, you might want to check out a new guide published this week about how businesses can use AI securely.




















































Let's personalize your content