Are cybercriminals lazy or brilliant for selling your passwords instead of using them?

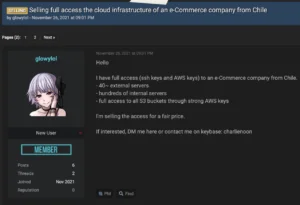
These cybercriminals, called initial access brokers (IABs), have the technical skills necessary to scope and compromise organizations—abilities that not all cybercriminals have. IABs gain access to an organization and then sell those credentials on hacker forums and the dark web, the part of the internet that isn’t accessible by search engines. Many of IABs’ target buyers already have ransomware or other malware, but need access to a place to deploy it.
IABs score the benefits without the risks
Cryptocurrency hides their identity
In 2021, there were 57% more IAB listings on hacker forums than the year prior, indicating that IABs aren’t slowing down anytime soon.
Criminals are also using cryptocurrency as a medium for this behavior. “Cryptocurrency privacy coins allow criminals to perform semi-anonymous transactions at scale, which has enabled all of these cybercrime markets in a big way,” said Greg Foss, cloud security researcher at Lacework.
“It’s a lot harder to track digital currencies like cryptocurrency than it is to track traditional payment methods like PayPal,” he said. Cryptocurrencies don’t need to be connected to real emails or bank accounts until they’re converted to fiat currency (e.g., the US dollar), which gives cybercriminals the power of anonymity. After a cybercriminal makes a big transaction, they can take tokens and pass them through cryptocurrency tumblers, which mix stolen coins with coins that were obtained legally, before transferring to an account from which they can withdraw fiat currency, making it extremely difficult to trace where the stolen coins came from.
Sometimes IABs are even company employees. Ransomware groups try to find employees currently working at their target companies, and ask people to plant and distribute their malware for a percentage of the profits in return.
They’re experts at determining the value of your credentials
IABs also target your credentials, for example, your username and password, so they can access your organization and assess how valuable that access is. IABs consider several factors to determine the value of the credentials they obtain. They assess the impact that the hack could have on the company’s brand and reputation if it were to be exposed. They also look at how much money the company has—if they have millions of dollars to spare, they’re more likely to be able and willing to pay a hacker to get their data back. They then consider how secure the business is in order to assess how long they could go without being detected and how much damage they could do in that period. If the IAB finds that the company is doing illegal things, or if they come across sensitive information, this also increases the value.
IABs use tried-and-true techniques to uncover valuable information
Dictionary attacks and brute force attacks are two popular methods that IABs use to compromise your account. Dictionary attacks are when hackers use a list of common passwords and check each one for a match. Brute force attacks are when they guess all possible combinations until they find the correct combination. As soon as an IAB finds your password for one account, they can use that password repeatedly on different websites. And if you’re like most people, you’ve used that password more than once. So the IABs aren’t just getting access to the site that they originally found your credentials for, they are hacking into several.
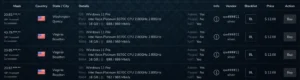
Once IABs have your credentials, they can access your cloud management infrastructure, web shells, secure shell, applications, or remote desktop protocol (RDP). RDP, a graphical interface used to connect with a Windows-based computer, is one of the most popular IAB offerings. It’s also one of the most profitable.
A few years ago, a notorious cybercriminal who went by “fxmsp,” sold the source code and credentials for hundreds of corporations, including top security companies like McAfee. Fxmsp was part of a cybercriminal group that scanned IP addresses to find open RDP ports and then used brute force attacks to guess the passwords. Fxmsp made more than $1.5 million over 3 years before being charged for fraud in 2018.
Don’t assume your cloud service provider is responsible for your data
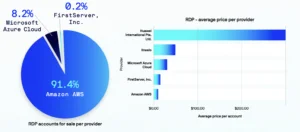
Ninety-one percent of the RDP accounts for sale across one of the primary marketplaces Lacework Labs investigated are credentials to log into AWS Elastic Compute Cloud (EC2) virtual computing environments. AWS EC2 provides users with virtual servers to run their infrastructure and applications.
AWS accounts are prime targets for cybercriminals because of the massive amounts of data they can contain. Cybercriminals can rack up a high bill on this tool that’s often used by businesses of all sizes.
IABs take advantage of the shared responsibility model to attempt to compromise AWS accounts. Shared responsibility means that both customers and cloud service providers are responsible for certain aspects of security. AWS protects the infrastructure that runs all of the services offered in the AWS Cloud, while customers must secure the data they store in the cloud. Unfortunately, not all customers are aware that they must protect their own data, and assume the service provider takes care of security. Because of this, customers are often affected by credential leakage, misconfigurations, and general security hygiene missteps, like failing to rotate their keys.
By default, AWS credentials are stored in predictable locations on your computer. If your computer is compromised, there’s a good chance that IABs would scan for your AWS credentials because they know exactly where to find them, and this process is often automated.
How to protect your accounts
Many people don’t even realize that they’ve been hacked until they see their bills. A few months ago, there was a rise in AWS accounts getting hacked, leaving owners stuck with significant bills. One user lost $55,000 from an AWS account that was compromised and hadn’t been used in two years, and another user was surprised with a $30,000 bill.
To prevent your accounts from being compromised by IABs or other criminals (before you see a massive bill and it’s too late), it’s important to follow a few key best practices:
- Create passwords that are at least 10 characters long and not any easily guessable phrase or combination. As password length increases, the time for cybercriminals to guess the password increases exponentially.
- Rotate master keys regularly—every 45-days is recommended and can be automated.
- Ensure multi-factor authentication is in place for all external-facing assets.
- Implement instance, billing, and utilization threshold limits with alerting and prevention.
- Monitor for internet-exposed vulnerabilities and patch them quickly and efficiently.
- Follow compliance standards and make sure to track notifications.
- Set up alerts for never-before-seen IP addresses that access your infrastructure.
- Look for changes in permissions, particularly new grants added to master keys.
It’s also important to stay up to date with the latest cybercriminal and IAB trends. I’m excited to hear the identity and access management sessions at AWS re:Inforce in Boston in a few weeks to learn more about the newest and most effective ways to keep my accounts safe. If you’ll be there too, let us know!
Categories
Suggested for you