Cloud Access: The Latest Offering for Initial Access Brokers
Lacework
JUNE 1, 2021
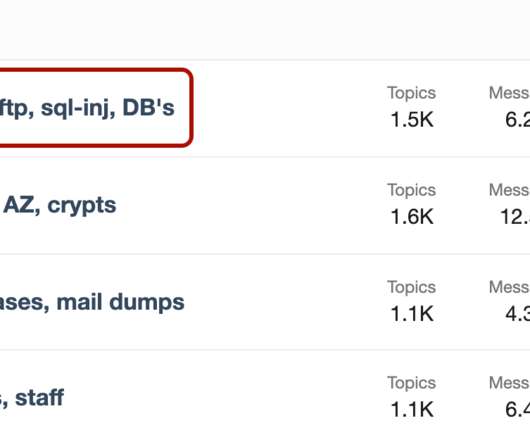
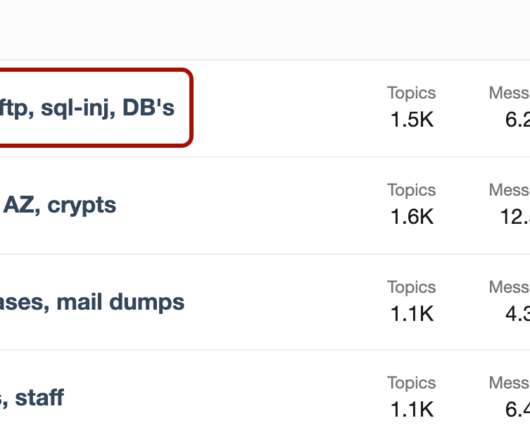
Summary Initial Access Brokers (IAB) have become commonplace across cybercrime marketplaces in recent years. The post Cloud Access: The Latest Offering for Initial Access Brokers appeared first on Lacework.



















































Let's personalize your content