Microsoft’s September 2023 Patch Tuesday Addresses 61 CVEs (CVE-2023-36761)

Microsoft addresses 61 CVEs including two vulnerabilities that were exploited in the wild.
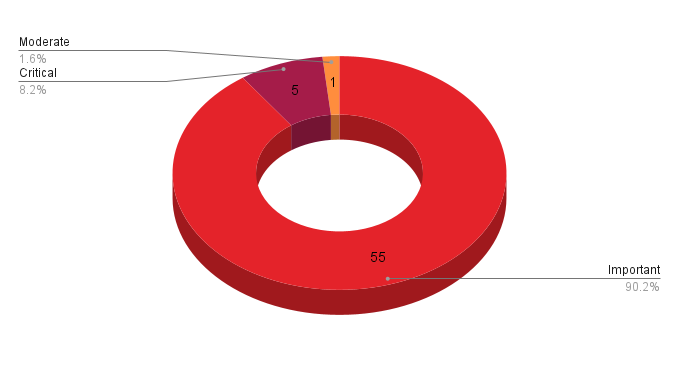
- 5Critical
- 55Important
- 1Moderate
- 0Low
Microsoft patched 61 CVEs in its September Patch Tuesday release, with five rated critical, 55 rated important and one rated moderate.
This month’s update includes patches for:
- .NET and Visual Studio
- .NET Core & Visual Studio
- .NET Framework
- 3D Builder
- 3D Viewer
- Azure DevOps
- Azure HDInsights
- Microsoft Azure Kubernetes Service
- Microsoft Dynamics
- Microsoft Dynamics Finance & Operations
- Microsoft Exchange Server
- Microsoft Identity Linux Broker
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Office Word
- Microsoft Streaming Service
- Microsoft Windows Codecs Library
- Visual Studio
- Visual Studio Code
- Windows Cloud Files Mini Filter Driver
- Windows Common Log File System Driver
- Windows Defender
- Windows DHCP Server
- Windows GDI
- Windows Internet Connection Sharing (ICS)
- Windows Kernel
- Windows Scripting
- Windows TCP/IP
- Windows Themes
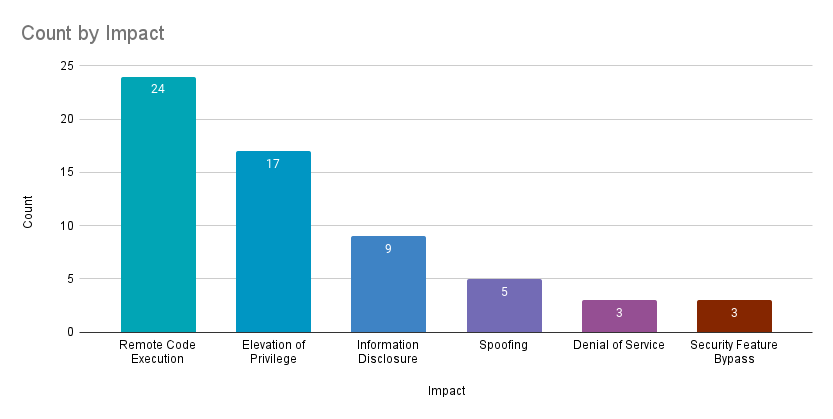
Remote code execution (RCE) vulnerabilities accounted for 39.3% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 27.9%.
CVE-2023-36761 | Microsoft Word Information Disclosure Vulnerability
CVE-2023-36761 is an information disclosure vulnerability in Microsoft Word. It was assigned a CVSSv3 score of 6.2 and is rated important. According to Microsoft, it has been exploited in the wild as a zero-day and was publicly disclosed prior to a patch being available. Its discovery is credited to the Microsoft Threat Intelligence team.
Microsoft says that the preview pane is an attack vector, meaning that simply previewing a specially crafted file can cause the exploit to trigger. Successful exploitation of this flaw would allow for the disclosure of New Technology LAN Manager (NTLM) hashes. NTLM hashes could be abused in NTLM relay or pass-the-hash attacks to further an attacker's foothold into an organization.
This is the second zero-day vulnerability disclosed this year that could result in the disclosure of NTLM hashes. In its March 2023 Patch Tuesday Release, Microsoft patched CVE-2023-23397, an elevation of privilege vulnerability in Microsoft Outlook that was also exploited in the wild as a zero-day. According to Microsoft, CVE-2023-23397 was exploited as a zero-day by a Russia-based threat actor.
CVE-2023-36802 | Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability
CVE-2023-36802 is an EoP vulnerability in the Microsoft Streaming Service Proxy. It was assigned a CVSSv3 score of 7.8 and is rated important. Exploitation of this flaw would grant an attacker SYSTEM privileges. According to Microsoft, it has been exploited in the wild as a zero-day. Discovery of this flaw is credited to Valentina Palmiotti from IBM X-Force, Quan Jin and ze0r with DBAPPSecurity WeBin Lab and both the Microsoft Security Response Center (MSRC) and Microsoft Threat Intelligence.
Palmiotti said in a post that a blog and exploit code for the vulnerability will “be released soon.”
Just saw that this vulnerability I reported to Microsoft was found to be exploited in the wild. Guess we are looking in the right places. Blog and exploit code to be released soon.https://t.co/zCxcs5x8Kb
— chompie (@chompie1337) September 12, 2023
CVE-2023-36744, CVE-2023-36745 and CVE-2023-36756 | Microsoft Exchange Server Remote Code Execution Vulnerability
CVE-2023-36744, CVE-2023-36745 and CVE-2023-36756 are RCE vulnerabilities affecting Microsoft Exchange. Each of these vulnerabilities were given CVSSv3 scores of 8.0 and were rated as “Exploitation More Likely” using the Microsoft Exploitability Index. Successful exploitation of these vulnerabilities requires an attacker to authenticate with LAN-access and have valid credentials for an Exchange user.
Including these three vulnerabilities, Microsoft has patched 13 other Exchange RCE vulnerabilities in 2023 thus far. Microsoft Exchange continues to be a sought after target for ransomware groups and advanced persistent threat (APT) actors. In the wake of vulnerabilities like ProxyLogon, ProxyShell and ProxyNotShell, it has become clear that attackers have their sights set on unpatched Microsoft Exchange Servers.
On August 3, a joint Cybersecurity Advisory (CSA) AA23-215A co-authored by multiple U.S. and international agencies was released to highlight the top routinely exploited vulnerabilities of 2022. The list contains 42 Common Vulnerabilities and Exposures (CVEs) known to be exploited by malicious actors which included 8 CVE’s affecting Microsoft Exchange Server. Patching of Microsoft Exchange Server vulnerabilities should be a top priority for any organization that utilizes it.
Separately, an information disclosure vulnerability, CVE-2023-36777, was also patched this month. This vulnerability was also rated as “Exploitation More Likely” and all four of these Exchange vulnerabilities were credited to Piotr Bazydlo of Trend Micro’s Zero Day Initiative.
CVE-2023-38143, CVE-2023-38144 | Windows Common Log File System Driver Elevation of Privilege Vulnerability
CVE-2023-38143 and CVE-2023-38144 are EoP vulnerabilities in the Windows Common Log File System (CLFS) Driver. Both CVEs were assigned a CVSSv3 score of 7.8 and are rated as “Exploitation More Likely.” An authenticated attacker could exploit these vulnerabilities to gain SYSTEM privileges.
With the addition of these two CVEs, seven EoP vulnerabilities were discovered in the Windows CLFS Driver in 2023, two of which were exploited in the wild as zero-days (CVE-2023-23376, CVE-2023-28252).
Tenable Solutions
A list of all the plugins released for Tenable’s September 2023 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's September 2023 Security Updates
- Tenable plugins for Microsoft September 2023 Patch Tuesday Security Updates
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
Related Articles
- Exposure Management
- Vulnerability Management
- Exposure Management




