Taking Control of Kubernetes: Enforcing Least Privilege to Secure Your Kubernetes Environment
Tenable
MARCH 18, 2024
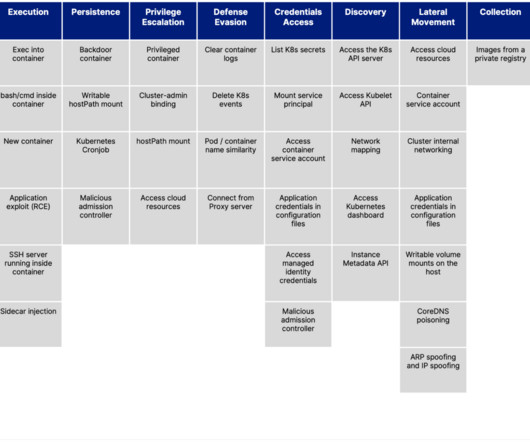
Kubernetes has become the de facto standard for managing containerized workloads in private and public clouds. However, security standards have failed to keep pace, leading to increased risk of cyberattacks and data breaches for insecure or misconfigured platforms.

















































Let's personalize your content