Tools like Sysmon and Osquery are useful in detecting anomalous behavior on endpoints. These tools give us good visibility of what’s happening on endpoints by logging multiple types of events, which we can forward to a SIEM or other correlation system for analysis.
In this blog series, we’ll analyze different malware families, looking at the types of events generated on the endpoint and how we can use Osquery to detect them.
Let's start!
Let’s start by analyzing the famous Emotet Banking Trojan, which is a continuous threat that targets a lot of countries and company sectors (The Evolution of Emotet). The dropper spreads through email phishing and downloads the malware using a malicious Office macro.
File samples:
https://app.any.run/tasks/b30d3215-a238-415e-ba7d-a884e1505758
https://www.virustotal.com/#/file/c932d54a9ef3c645a28b7d8de9747fc6c06fc23c6d65c036da4eae4d778a81db
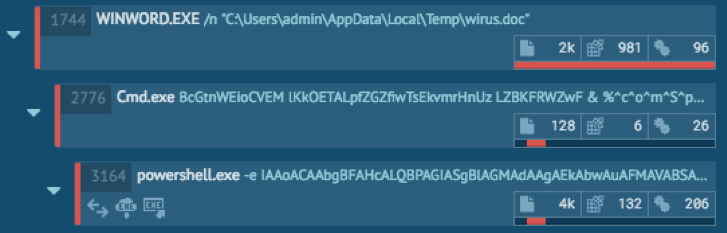
As we can see in the sandbox report, the Office macro executes PowerShell with an encoded command to download the payload.
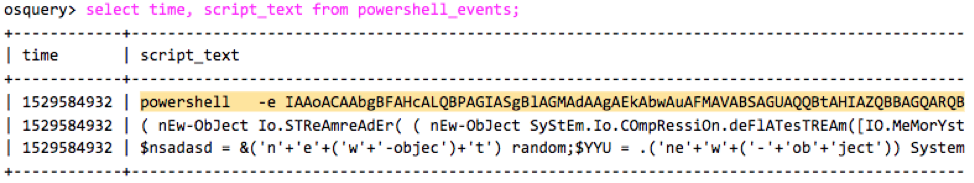
If we run the sample in our environment with Osquery installed, we can build a query to retrieve events generated by PowerShell from the powershell_events table. Osquery reads the Microsoft-Windows-PowerShell eventlog channel, so you need to enable Script block logging.
We can see the encoded PowerShell command and also the script text code generated after decoding the command.
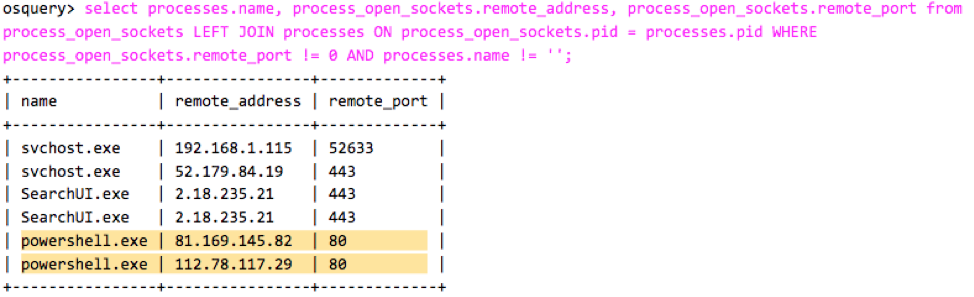
Once PowerShell is downloading the payload, Osquery can log socket connections opened by any process. We can do an easy JOIN between process_open_socket table and processes table to see which processes are making network connections.
It’s interesting to see which files have been written on disk during the payload download. To do so, we can query the file table that stores some useful fields (file table schema). This table needs a WHERE condition to return results, so we can add some filters like Users directory and files created in the last 100 seconds for example.
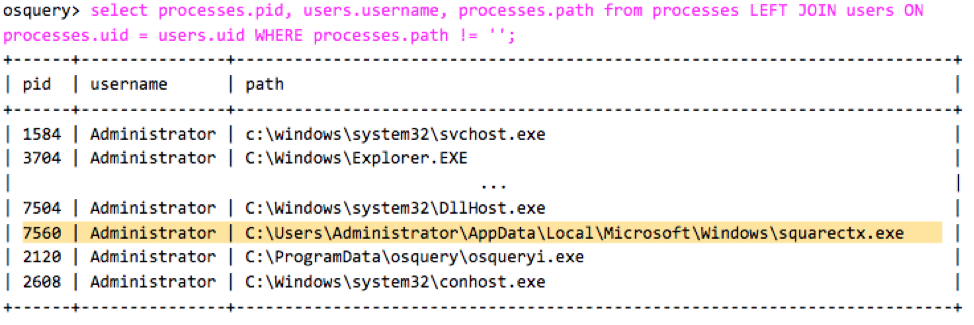
The downloaded file from PowerShell is a Emotet dropper that extracts the final payload and executes it (squarectx.exe). Now, let’s query the system running processes. Similar to above, we can do a JOIN with users table to see the username column. Some rows have been omitted for a cleaner view.
Now we know that Emotet malware is running in our environment and probably is doing malicious things, so let’s look for signs of malware activity. For that, we reuse the query we used above to see network connections from system processes. Here, we can detect communication to the Command and Control server.
As we have seen, it is possible to analyze malware and extract valuable information using tools like Osquery that give us rich visibility of systems events.
How AlienVault uses Osquery
Osquery allows you to retrieve a wealth of events and useful information from your endpoints. This can be extremely helpful for investigating security incidents as well as threat hunting activities on your critical assets.
AlienVault leverages Osquery through the AlienVault Agent to enable threat hunting in both USM Anywhere and the Open Threat Exchange.
The AlienVault Agent is a lightweight, adaptable endpoint agent based on Osquery and maintained by AlienVault. In USM Anywhere, the AlienVault Agent enables continuous endpoint monitoring, using the built-in AlienVault threat intelligence to automate endpoint queries and threat detection alongside your other network and cloud security events. This allows USM Anywhere to deliver endpoint detection and response (EDR), file integrity monitoring (FIM), and rich endpoint telemetry capabilities that are essential for complete and effective threat detection, response, and compliance.
Try it for yourself in the USM Anywhere Online Demo.
In April, AlienVault introduced the Endpoint Threat Hunter – a free threat-scanning service in Open Threat Exchange® (OTX™) based on the AlienVault Agent. OTX Endpoint Threat Hunter allows anyone to determine if their endpoints are infected with the latest malware or other threats by manually scanning their endpoints for the presence of indicators of compromise (IoCs) that are catalogued in OTX.
Get started with OTX Endpoint Threat Hunter Free: https://otx.alienvault.com/endpoint-threat-hunter/welcome
Here is an example of how we detected Emotet infection on an analysis system using OTX Endpoint Threat Hunter.

Stay tuned!
Appendix
Queries
select time, script_text from powershell_events;
select processes.name, process_open_sockets.remote_address, process_open_sockets.remote_port from process_open_sockets LEFT JOIN processes ON process_open_sockets.pid = processes.pid WHERE process_open_sockets.remote_port != 0 AND processes.name != '';
select path, size, from file where path like 'C:Users%%' and mtime > (select local_time from time) - 100 and filename != '.';
select processes.pid, users.username, processes.path from processes LEFT JOIN users ON processes.uid = users.uid WHERE processes.path != '';
c932d54a9ef3c645a28b7d8de9747fc6c06fc23c6d65c036da4eae4d778a81db
9f6325ebce797b5ceec1bbf32e61aec8fbe8b650
124d03b86227bbf282f0f567ae11858e
bafc6731efd63f57c89653b24ba532ac1e96d259993c8f3d96d26e1cf6cd57d3
DNS requests
samoticha.de
okane-mikata.com
Connections
81.169.145.82
112.78.117.29
184.186.78.177
74.139.102.161
OTX