The Six Pillars of Effective Security Operations
Palo Alto Networks
JANUARY 7, 2020
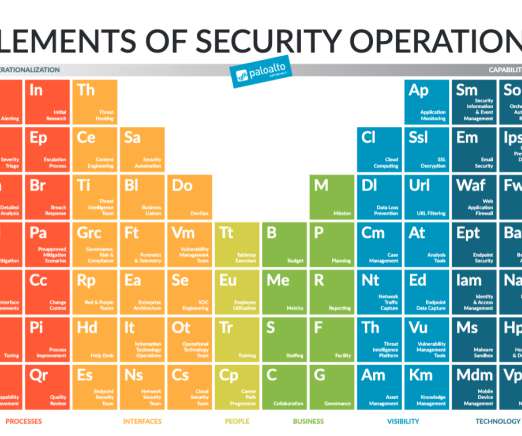
In our extensive work with security teams around the world, we’ve seen the best and the worst security operations (SecOps) practices. The first measure to make meaningful improvement is to take a step back and do an honest evaluation of how your security operations are structured and how they’re serving your business goals.











Let's personalize your content