How to protect containers from Living Off the Land (LOTL) attacks: A step-by-step guide
Lacework
MARCH 6, 2024
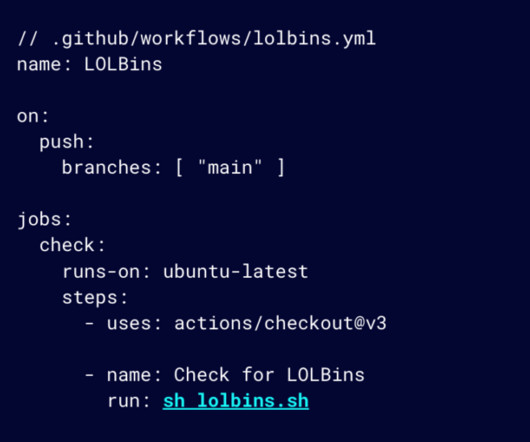
While there are many categories in the GTFOBins catalog, this article will focus on sudo and SUID. This is because when we talk about LOTL, an attacker likely already has access to the system, and they are probably trying to elevate their privilege or set up persistence within a system. This is where the SUID bit flag comes into play.














Let's personalize your content