The Good and the Bad of Databricks Lakehouse Platform
Altexsoft
MARCH 30, 2023
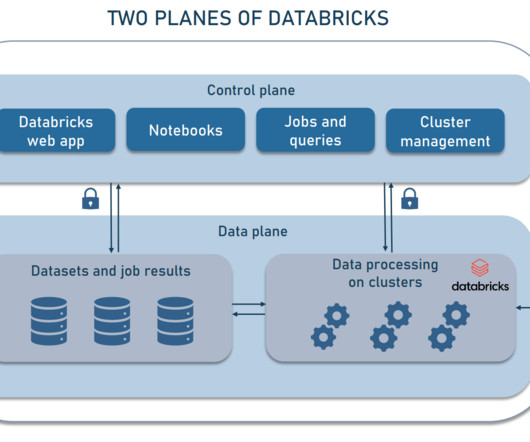
But what do the gas and oil corporation, the computer software giant, the luxury fashion house, the top outdoor brand, and the multinational pharmaceutical enterprise have in common? Data experts log into the workspaces using a single sign-on (SSO) authentication to build data pipelines, write SQL queries, design ML models, and so on.













Let's personalize your content