To Boost Software Supply Chain Security, Stop the Finger-Pointing
Tenable
OCTOBER 27, 2022
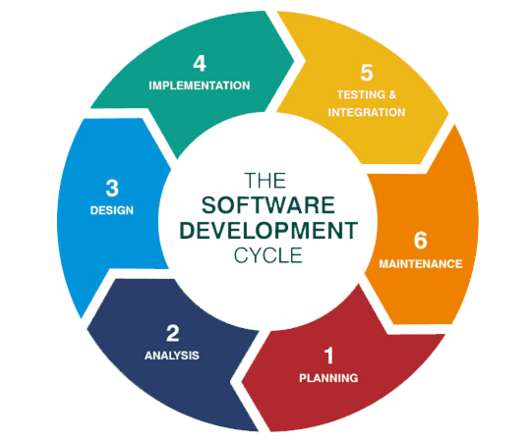
For the first time in eight years, the “Accelerate State of DevOps Report” from Google’s DevOps Research and Assessment (DORA) team zooms in on software supply chain security. Some of respondents’ most widely adopted SDLC security practices were: . Monitoring public information regarding software vulnerabilities.



















Let's personalize your content