How Netflix uses eBPF flow logs at scale for network insight
Netflix Tech
JUNE 7, 2021
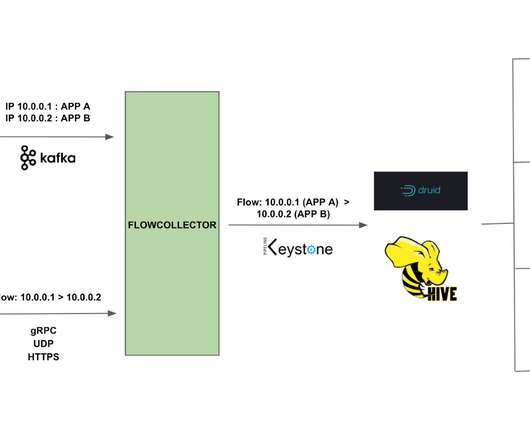
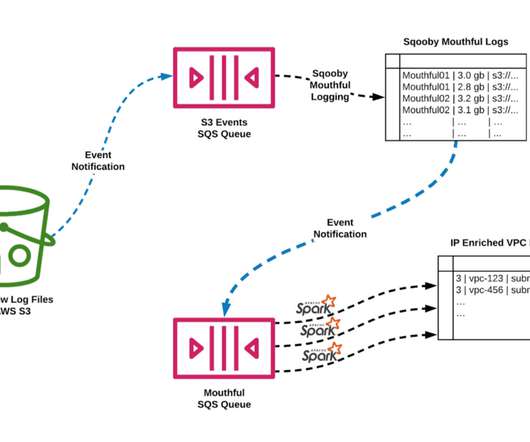
At much less than 1% of CPU and memory on the instance, this highly performant sidecar provides flow data at scale for network insight. Flow Exporter The Flow Exporter is a sidecar that uses eBPF tracepoints to capture TCP flows at near real time on instances that power the Netflix microservices architecture. What is BPF?













Let's personalize your content