Demystifying the Modern Data Stack
Dataiku
OCTOBER 1, 2021
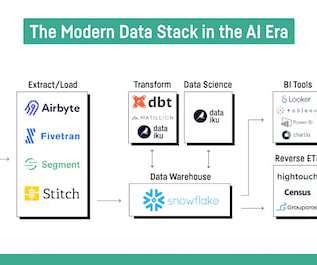
If you’re looking to leverage data at a small or midsize business (or even in a smaller business unit or a larger enterprise), you’ve no doubt heard of the modern data stack — a suite of tools or a pipeline that makes for easier collection, operationalization, and analysis of data.

















Let's personalize your content