Hunting Rootkits with eBPF: Detecting Linux Syscall Hooking Using Tracee
Aqua Security
APRIL 21, 2022
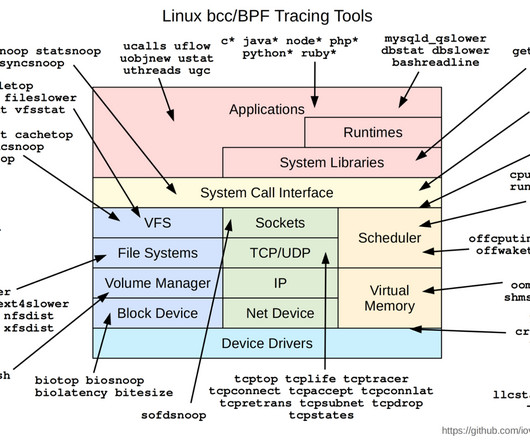
Today, cloud native platforms are increasingly using eBPF-based security technology. It enables the monitoring and analysis of applications’ runtime behavior by creating safe hooks for tracing internal functions and capturing important data for forensic purposes.













Let's personalize your content