5 practical tips to lock up your Kubernetes security
Lacework
SEPTEMBER 8, 2022
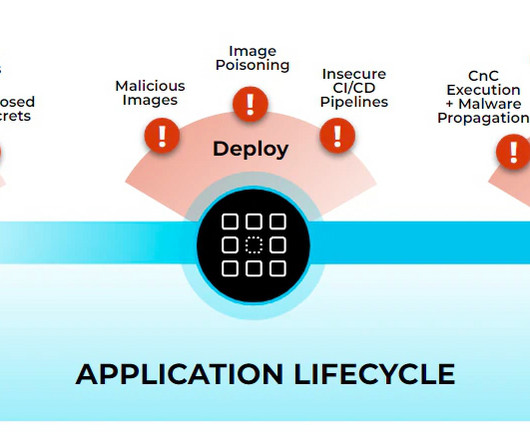
Kubernetes is quickly becoming the leading container orchestration and management technology. In fact, 94% of respondents admitted to experiencing a security incident in their K8s environment in the last 12 months, according to the State of Kubernetes Security Report. . But you do want to start somewhere. .














Let's personalize your content