SDLC Requirement Analysis – All You Need to Know
Openxcell
FEBRUARY 14, 2021
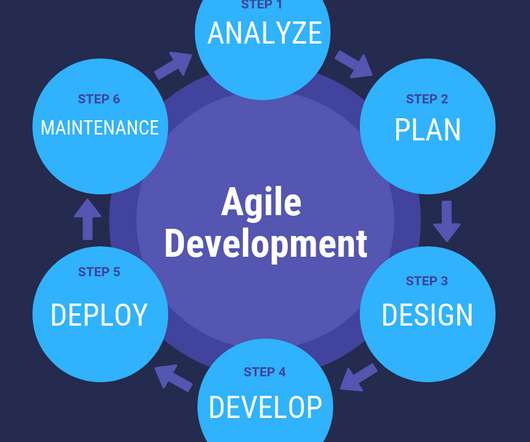
SDLC Requirement Analysis plays a crucial role in it. Requirement Analysis is an important phase of SDLC. A reasonable product delivery demands correct requirements gathering, the efficient examination of requirements gathered, and clear requirement documentation as a precondition. What is SDLC (Software Development Life Cycle)?
















Let's personalize your content