How to Develop IoT Applications: A Complete Guide for 2022
The Crazy Programmer
APRIL 24, 2022
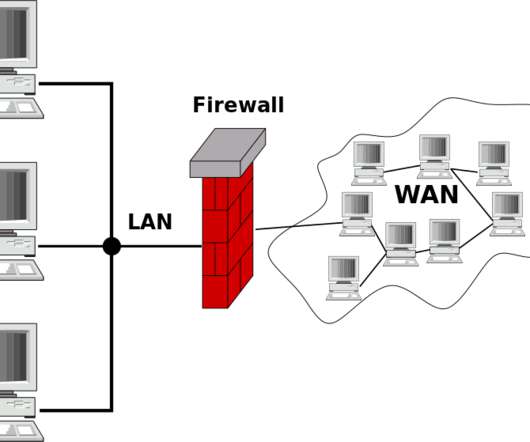
People create IoT applications; people use IoT applications—the world’s technology grows from the internet to the Internet of Things, from middlemen transaction processes to Smart Contracts. How do you develop IoT applications ? Network links include MQT, wireless, LAN, Bluetooth, WiFi, and HTTP.

















Let's personalize your content