Transparent Security Outperforms Traditional DDoS Solution in Lab Trial
CableLabs
MAY 20, 2021
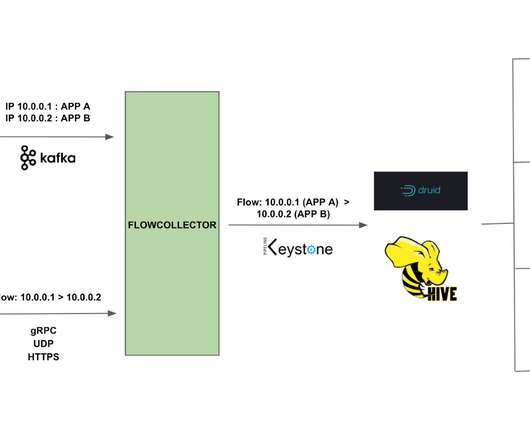
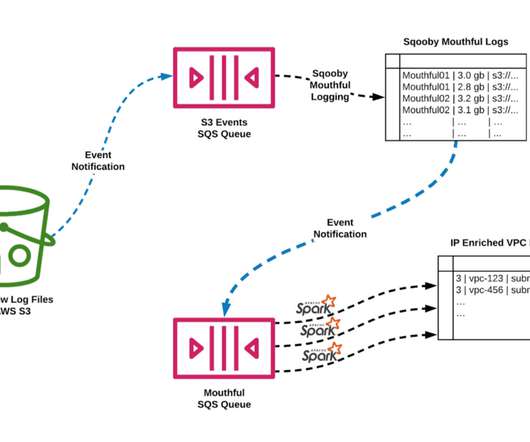
P4”-based) and uses in-band network telemetry (INT) technology for device identification and mitigation, blocking attack traffic where it originates on the operator’s network. We initially released the Transparent Security architecture and open-source reference implementation in October 2019.















Let's personalize your content