Cathay Pacific to take cloud journey to new heights
CIO
JANUARY 8, 2024
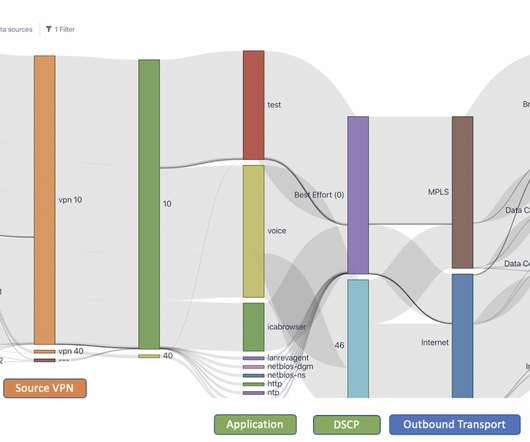
Cathay’s move to a modern SASE will deliver reliable internet bandwidth, enhanced interoperability between network elements, and enable the airliner to better manage and secure hundreds of workloads on AWS and Azure, Nair says. It will replace the standard MPLS network, he adds.


















Let's personalize your content