10 Vitals To Get Successful Results In Software Development
Xicom
MAY 30, 2021
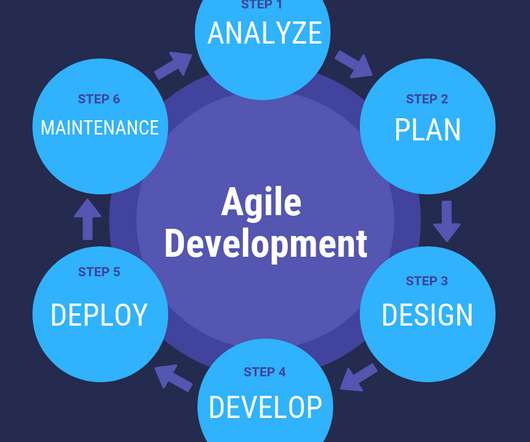
Whether you are a business owner or a CTO, you are solely responsible for the successful execution of the software development project. Even though design and software development companies in the UAE thrive on delivering the demands of their clients, still retaining their life and rationality. What Is Software Development Process?
























Let's personalize your content