AoAD2 Practice: Evolutionary System Architecture
James Shore
MAY 31, 2021
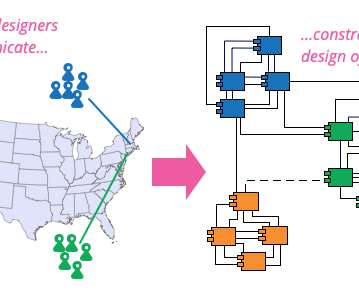
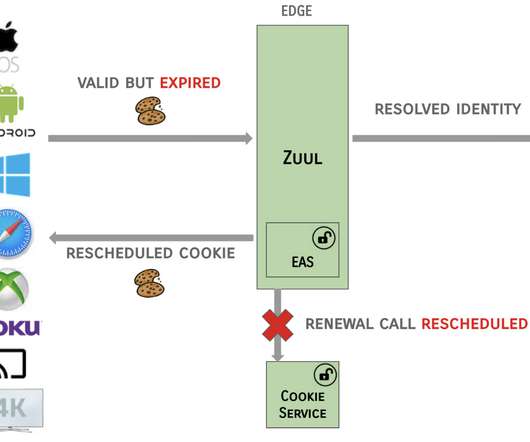
To share your thoughts, join the AoAD2 open review mailing list. Evolutionary System Architecture. What about your system architecture? By system architecture, I mean all the components that make up your deployed system. When you do, you get evolutionary system architecture.






















Let's personalize your content