Visualizing Traffic Exit Points in Complex Networks
Kentik
SEPTEMBER 19, 2018
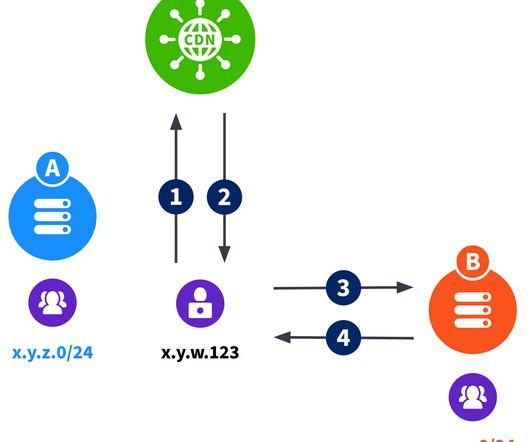
It’s that “exit point” question in particular that led Kentik to build our BGP Ultimate Exit feature set (UE for short). In a nutshell, UE enriches all the flow data Kentik receives with tags that indicate the PoP, router, interface, etc. Kentik’s ingest layer maintains a full BGP table from each router.
















Let's personalize your content