What the Digital Operational Resilience Act means for you
CIO
MARCH 18, 2024
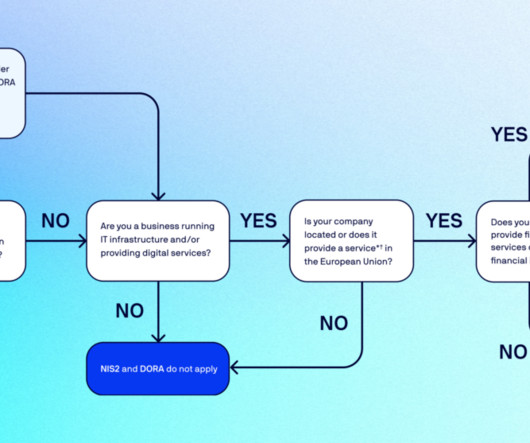
As security risks grow more complex, government agencies are emphasizing new regulations to help lay out what businesses need to do to protect their IT infrastructure while also establishing IT security standards. Moving forward, businesses will need to take a much closer look at the IT environments they utilize.



















Let's personalize your content