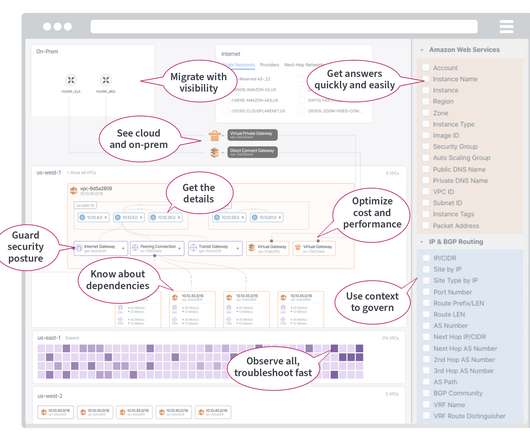
How to Monitor Traffic Through Transit Gateways
Kentik
JUNE 21, 2021
Check out The Network Pro’s Guide to the Public Cloud ebook for a quick tutorial on AWS cloud networking.). Cloud architects and network engineers can interact directly on the map to view hop by hop, metrics, and details on traffic, routing, and metadata.















Let's personalize your content