AWS vs. Azure vs. Google Cloud: Comparing Cloud Platforms
Kaseya
MAY 13, 2021
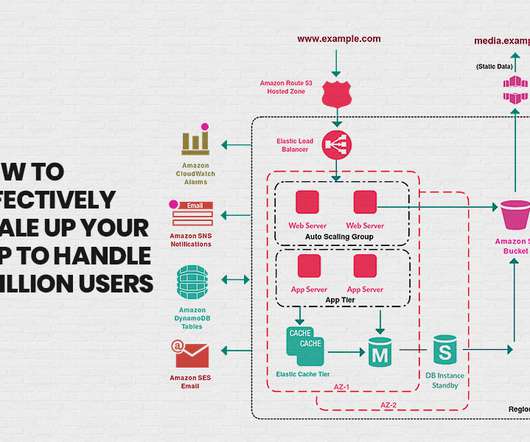
In a public cloud, all of the hardware, software, networking and storage infrastructure is owned and managed by the cloud service provider. The public cloud infrastructure is heavily based on virtualization technologies to provide efficient, scalable computing power and storage. What Are the Advantages of Azure Cloud?





























Let's personalize your content