pdflayer API Review – HTML to PDF Conversion API for Developers
The Crazy Programmer
APRIL 6, 2021
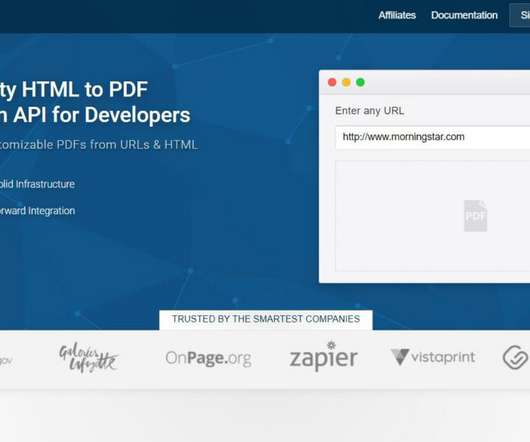
pdflayer combines several powerful PDF engines based on browsers running stalwart operating systems. Before transferring URL to any API parameters, it is advised to URL encode URL. The API is highly convenient to use even for a non-technical person. Robust PDF Engine. Powerful CDN. Tracking Statistics. Cheers to pdflayer!






























Let's personalize your content