My New Year’s Resolution: Going Passwordless!
Ivanti
DECEMBER 29, 2021
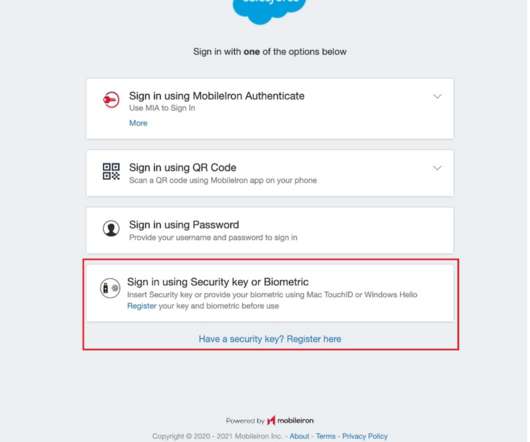
Another best practice that I started several years ago was to adopt a passwordless authentication initiative for all my internet connected personal devices. Fortunately for me, my company began enforcing zero sign-on authentication along with deploying a multi-layered anti-phishing protection system several years back.





















Let's personalize your content