9 Types of Phishing and Ransomware Attacks—And How to Identify Them
Ivanti
JANUARY 19, 2022
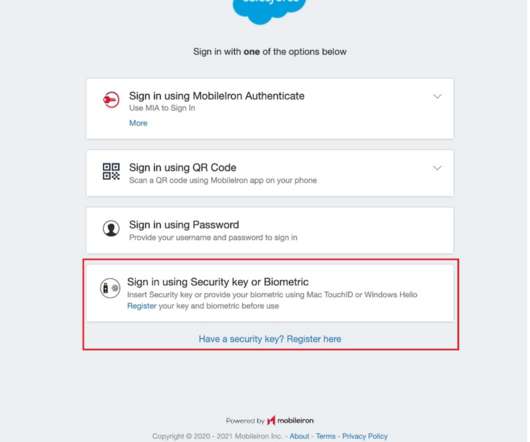
End users are easily coaxed into divulging their precious personal information because of attention-grabbing headlines and authentic-looking, obfuscated or shortened hyperlinks. Pharming employs authentic-looking hyperlinks in phishing emails that redirect end users from a specific, legitimate site to a malicious one?by


























Let's personalize your content