AWS Disaster Recovery Strategies – PoC with Terraform
Xebia
DECEMBER 21, 2022
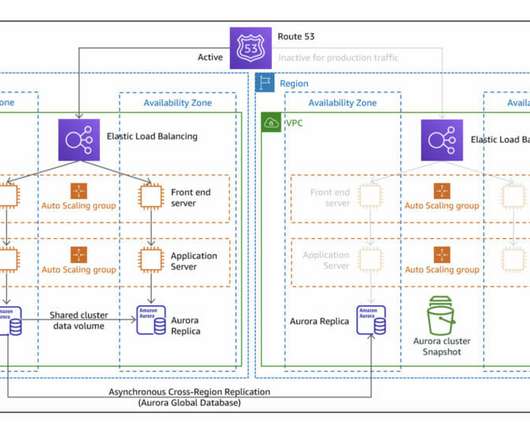
The project will generate a subset of the following diagram ( source: AWS Disaster Recovery Workloads ). This exercise consists of iterations through each one of them while understanding its differences. Backup service repository. RPO is the acceptable time frame from the last data recovery point. Pilot Light.




















Let's personalize your content