Firewalla launches its Purple gigabit home firewall
TechCrunch
FEBRUARY 1, 2022
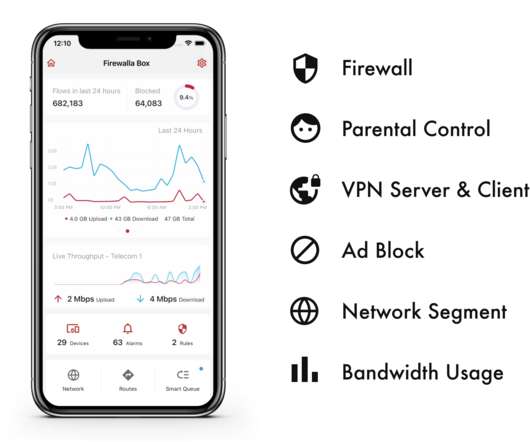
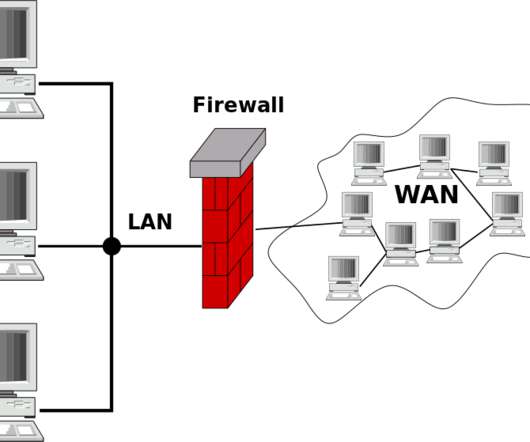
Over the course of the last few years, Firewalla ‘s combined firewall and router devices have made a name for themselves as the go-to hardware security tools for many enthusiasts and small businesses. With many homes now having access to gigabit internet connections, though, the Purple slots in nicely in the middle there.

















Let's personalize your content