Optimizing Network Stability and Reliability Through Data-Driven Strategies
Kentik
APRIL 24, 2023
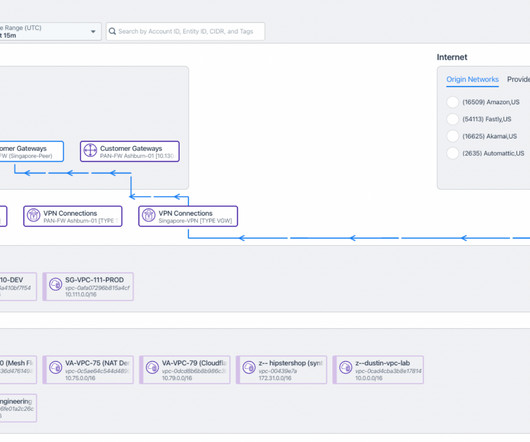
Rather than collecting only flow data from routers, or only eBPF information from containers, the fact that application traffic traverses so many devices means we need much more data to get an accurate view of what’s happening. The Kappa Host agent deployed to collect kernel information and return it to the Kentik platform.



















Let's personalize your content