Strategies for Managing Network Traffic from a Remote Workforce
Kentik
MARCH 19, 2020
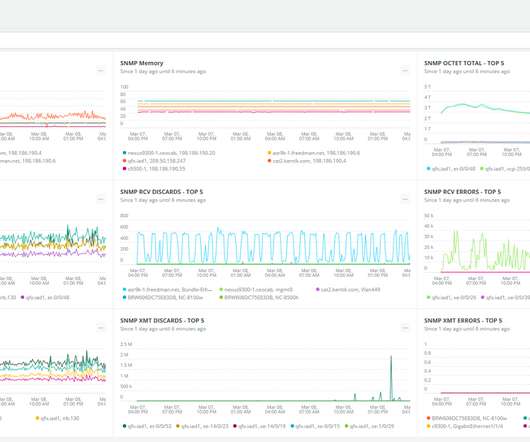
In many infrastructures, the inflection points are at the network edge, where VPN gateways authenticate and encrypt remote-access traffic. This could mean the users are saturating the internet connectivity or that they’ve saturated the LAN (or maybe WAN). The richest data sources are from the VPN devices or firewalls.


















Let's personalize your content