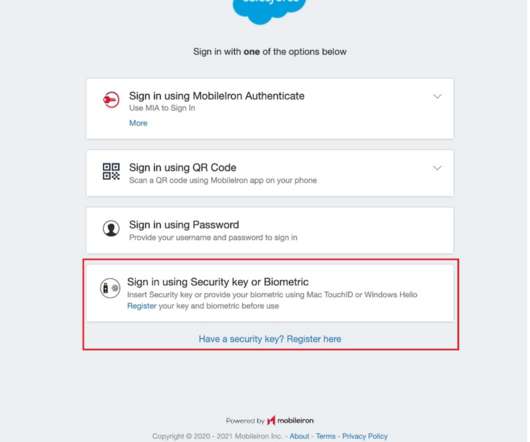
What is Tailgating in Cyber Security
The Crazy Programmer
NOVEMBER 28, 2021
The main goal of tailgating is to enter the local place with no proper authentication. They may even install spyware in the computer devices of the organizations. Firstly, companies need to make strong policies in the workplace and use advanced access control at the entrance. Want to know what tailgating is in cyber security?





















Let's personalize your content