Business Values and Adoption of ServiceNow BCM
Perficient
MARCH 27, 2023
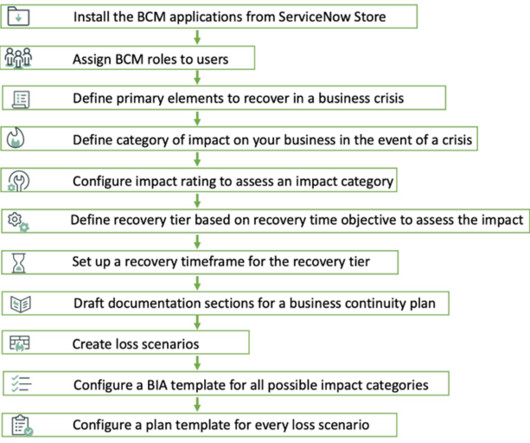
Business Continuity Management (BCM) is a framework and process for identifying and addressing risks to an organization’s business operations, ensuring business continuity during disruptions, and facilitating recovery afterward.

















Let's personalize your content