Radically simplify and expand Zero Trust to cloud workload
CIO
DECEMBER 21, 2023
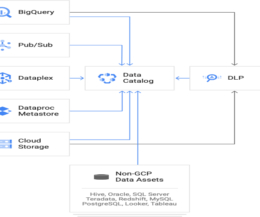
However, securing the cloud traffic from these workloads is a complex task, as cloud adoption increases, and the number of mission-critical workloads spread across multiple cloud providers. One of the most significant areas that organizations are revisiting is secure cloud and workload connectivity.




























Let's personalize your content