ChatGPT and Checkov: Fix IaC Security Issues Fast
Prisma Clud
JUNE 27, 2023
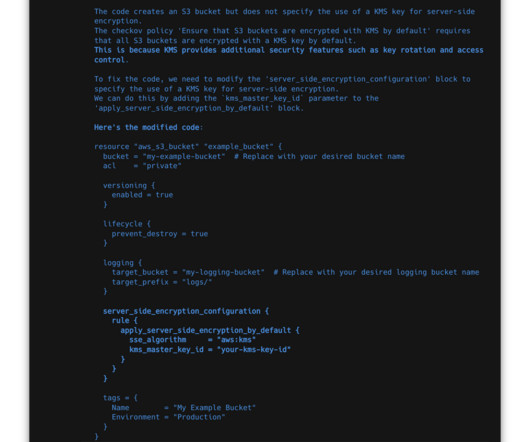
One such open-source IaC scanning tool, Checkov , has gained popularity due to its ability to scan IaC code written in Terraform, Kubernetes, CloudFormation and other popular IaC languages. In the Checkov context, ChatGPT aids in analyzing potential issues found in IaC code and offers suggestions on how to fix them.


















Let's personalize your content