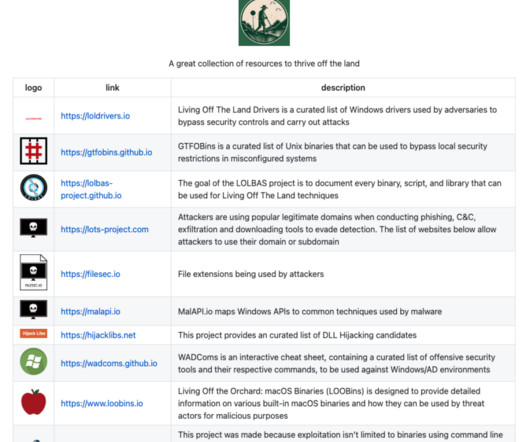
An overview of Living Off the Land (LOTL) attack techniques
Lacework
MARCH 6, 2024
Unlike traditional malware, LOTL techniques exploit trusted system tools already present in the environment, making detection incredibly difficult. This project focuses specifically on cataloging Microsoft-signed binaries that can be exploited for malicious purposes on Windows systems. The overall concept remains the same (i.e.,
























Let's personalize your content