Push Security launches to make SaaS sprawl and shadow IT safer
TechCrunch
JULY 19, 2022
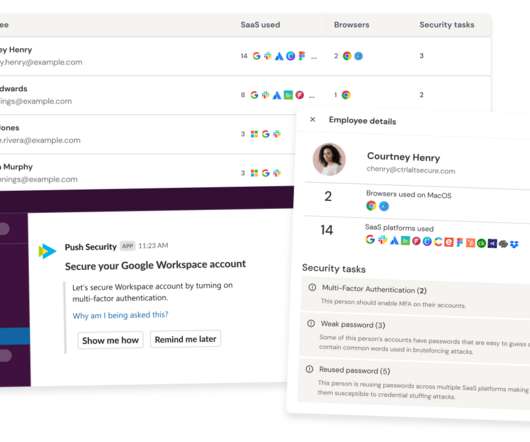
In practice, this could mean that marketing teams test-driving third-party social media management tools could inadvertently jeopardise the company’s Twitter and Facebook accounts, or admins could dabble with mobile device management (MDM) software and create an easy inroad for hackers to deploy malware to mobile devices across the workforce.


















Let's personalize your content