AWS Disaster Recovery Strategies – PoC with Terraform
Xebia
DECEMBER 21, 2022
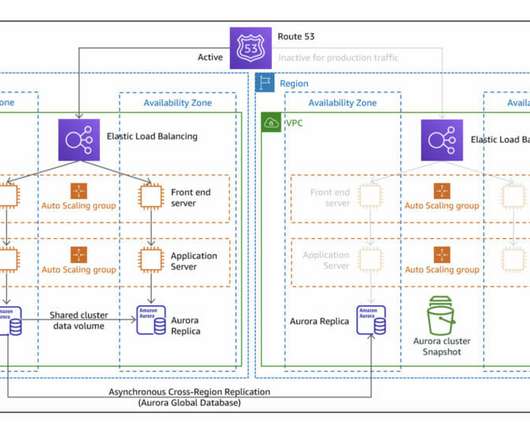
The project will generate a subset of the following diagram ( source: AWS Disaster Recovery Workloads ). In this PoC, we will create the front-end layer of a three-tier architecture. This exercise consists of iterations through each one of them while understanding its differences. Pilot Light strategy diagram.
























Let's personalize your content