4 paths to sustainable AI
CIO
JANUARY 31, 2024
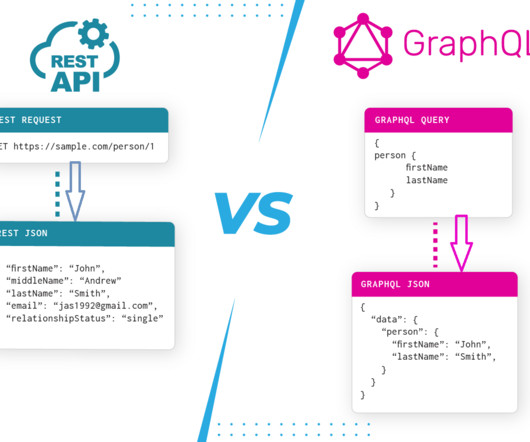
Use more efficient processes and architectures Boris Gamazaychikov, senior manager of emissions reduction at SaaS provider Salesforce, recommends using specialized AI models to reduce the power needed to train them. “Is He also recommends tapping the open-source community for models that can be pre-trained for various tasks.






















Let's personalize your content