CCNA vs CCNP – Detailed Guide and Differences
The Crazy Programmer
JUNE 17, 2022
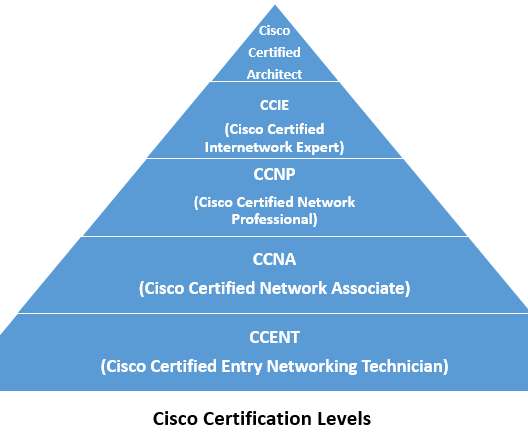
CCNA and CCNP, both are Cisco approved certification courses, which are very popular among those who seek a career in the computer networking line. Cisco is a very reputed and well-settled organization that manufactures and sells network-related equipment and solutions. Cisco Certified Network Associate (CCNA).















Let's personalize your content