Managed Services for Enhanced Network Security, Endpoint-to-Endpoint
CIO
JULY 11, 2022
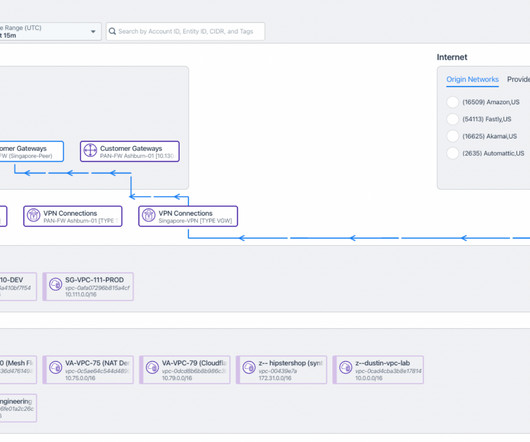
To that end, IT leaders need to focus on implementing integrated network and security solutions to connect users, devices and partners to applications and data within the public cloud and private data centers across the globe. The basic firewall functionality may not be enough to help protect enterprise networks.


























Let's personalize your content