Five Reasons for Migrating HBase Applications to the Cloudera Operational Database in the Public Cloud
Cloudera
SEPTEMBER 1, 2022
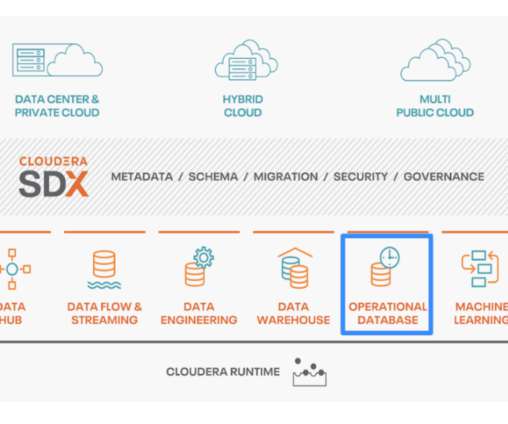
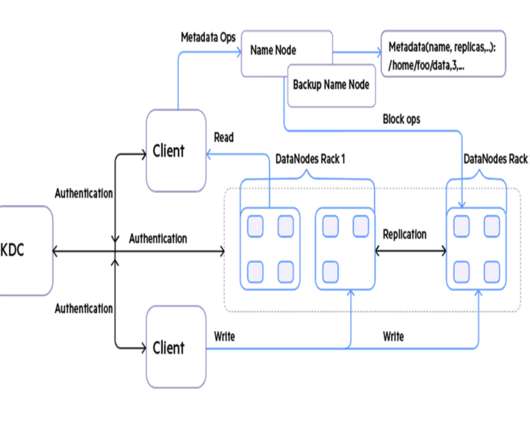
While application developers and database admins are well aware of the benefits of using HBase, they also know about a few shortcomings that the database has historically had. COD offers a clear pathway for developers and admins that are looking for a friction-free way to migrate existing HBase applications to the public cloud.




















Let's personalize your content