DocRaptor Review – HTML to PDF API
The Crazy Programmer
OCTOBER 8, 2020
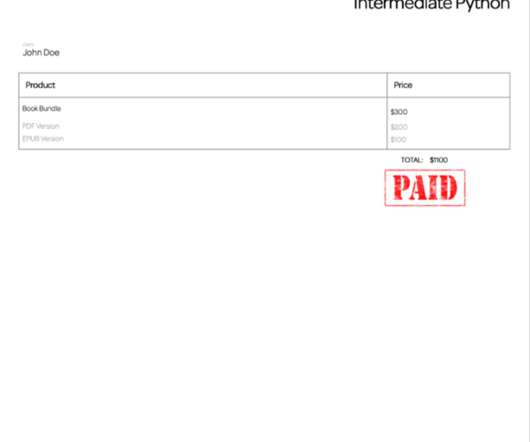
Here, in this article, we’ll review the DocRaptor tool, an HTML to PDF API converter. The DocRaptor review will briefly discuss how it works with Python, some code examples, features, benefits, and perhaps pros and cons. DocRaptor API provides a 99.999% uptime speed with high reliability and service, highly trusted in the market.


















Let's personalize your content