What is Gateway in Computer Network – Types, Examples, Functions
The Crazy Programmer
SEPTEMBER 25, 2021
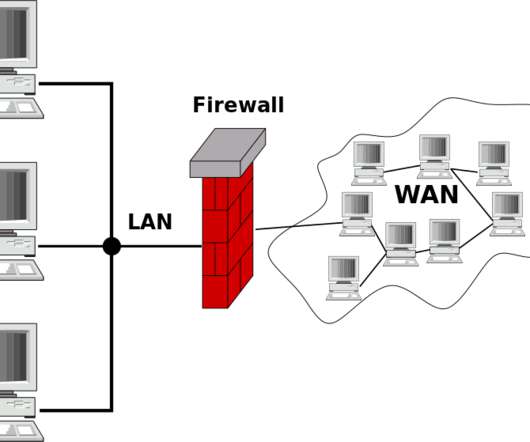
These devices can be the firewall, router, server, and other devices used for the networking and allow the flow of the data from one device to another device through their network. VoIP Trunk Gateway. The VoIP Trunk gateway is still used. Web Application Firewalls. Types of Gateway. Conclusion.




















Let's personalize your content