Top 10 Kubernetes Application Security Hardening Techniques
Aqua Security
AUGUST 18, 2021
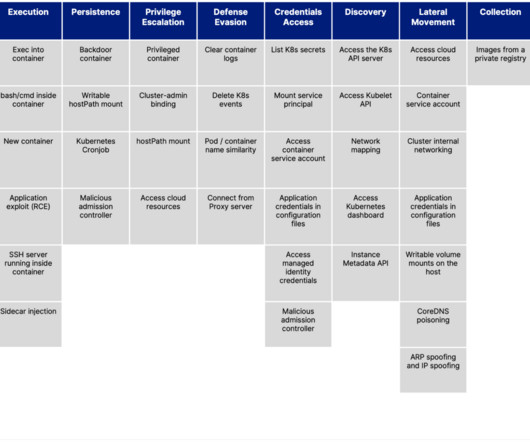
One of the main challenges developers face is how to manage security risks when deploying applications to Kubernetes clusters. A great way to address this early is by applying security hardening to the application manifests during the development process.




















Let's personalize your content